Services Guide
Introduction to our Services Guide
This Services Guide contains provisions that define, clarify, and govern the scope of the services described in the quote that has been provided to you (the “Quote”), as well as the policies and procedures that we follow (and to which you agree) when we provide a service to you or facilitate a service for you. If you do not agree with the terms of this Services Guide, you should not sign the Quote and you must contact us for more information.
This Services Guide is our “owner’s manual” that generally describes all managed services provided or facilitated by Cloud Matrix IT, LLC (“Cloud Matrix IT,” “we,” “us,” or “our”); however, only those services specifically described in the Quote will be facilitated and/or provided to you (collectively, the “Services”).
This Services Guide is governed under our Master Services Agreement (“MSA”). You may locate our MSA through the link in your Quote or, if you want, we will send you a copy of the MSA by email upon request. Capitalized terms in this Services Guide will have the same meaning as the capitalized terms in the MSA, unless otherwise indicated below.
Activities or items that are not specifically described in the Quote will be out of scope and will not be included unless otherwise agreed to by us in writing. Please read this Services Guide carefully and keep a copy for your records.
Initial Audit / Diagnostic Services
In the Initial Audit/Diagnostic phase of our services, we audit your managed information technology environment (the “Environment”) to determine readiness for, and compatibility with, ongoing managed services.
Our auditing services may include:
• Audit to determine general Environment readiness and functional capability
• Review of hardware and software configurations
• Review of current vendor service and warranty agreements
• Basic security vulnerability check
• Backup and file recovery solution audit
• Internet speed and ISP audit
• Print output audit
• Office telephone vendor audit
• Asset inventory
• Email and website hosting audit
• IT support process audit
If deficiencies are discovered during the auditing process (such as outdated equipment or unlicensed software), we will bring those issues to your attention and discuss their potential impact on the Services. We will also provide options to address those deficiencies.
Unless otherwise expressly agreed by us in writing, auditing services do not include the remediation of any issues, errors, or deficiencies, and we cannot guarantee all issues will be identified during the audit. Issues discovered after the audit may be addressed in future Quotes.
Onboarding Professional Services
In the Onboarding phase of our services, we prepare your IT environment for the monthly managed services described in the Quote. During this phase, we work closely with your Authorized Contact(s) to gather the information needed to properly configure your systems.
Our onboarding tasks may include:
• Removal of previous IT provider tools or monitoring agents
• Inventory of all protected devices (servers, workstations, laptops)
• Installation of our endpoint protection and remote support agents
• Configuration of patch management and security updates
• Uninstallation of unsafe or unnecessary applications
• Performance optimization scans and disk cleanup
• Firewall and network configuration review
• Verification of backup power (UPS) on mission-critical devices
• Documentation of current server environment
• Evaluation of business continuity and backup plans
• Password policy and user credential review
This list is subject to change if we determine, at our discretion, that different or additional onboarding activities are required.
We may make additional recommendations during onboarding if we identify changes needed to support your managed services effectively. If deficiencies are discovered during the onboarding process, we will bring those issues to your attention and discuss the impact of the deficiencies on our provision of our monthly managed services. Please note, unless otherwise expressly stated in the Quote, onboarding-related services do not include the remediation of any issues, errors, or deficiencies (“Issues”), and we cannot guarantee that all Issues will be detected during the onboarding process.
The duration of the onboarding process depends on many factors, many of which may be outside of our control—such as product availability/shortages, required third party vendor input, etc. As such, we can estimate, but cannot guarantee, the timing and duration of the onboarding process. We will keep you updated as the onboarding process progresses.
Ongoing / Recurring Services
Ongoing/recurring services are services that are provided to you or facilitated for you on an ongoing basis and, unless otherwise indicated in a Quote, are billed to you monthly 30 days in advance of those services being rendered. Some ongoing/recurring services will begin with the commencement of onboarding services; others will begin when the onboarding process is completed. Minimum contract length is 12 months as most of our licensing is purchased in 12 month cycles. Please direct any questions about start or “go live” dates to your account manager/vCIO.
Managed Technology Services
Advanced Automated System Patching
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides proactive, automated patch management services using an enterprise-grade platform. This solution ensures your systems remain up-to-date, secure, and compliant by regularly applying critical operating system updates and security patches.
Service Scope
• Automated Patch Deployment: We configure and maintain automated workflows to scan, detect, and deploy updates to supported operating systems on a regular cadence. Patch cycles are scheduled during maintenance windows to minimize user disruption.
• Policy-Based Management: Updates are deployed according to predefined policies, which allow us to:
o Approve or defer specific patches and/or drivers
o Schedule patching based on device groups or business units
o Handle reboots intelligently based on the type of update and user activity
• Monitoring & Remediation: We continuously monitor patch deployment success, failed installations, and systems that are out of compliance. Our team takes corrective action when necessary to resolve issues and ensure patch coverage.
• Reporting & Visibility: Clients may request reporting on patch status and compliance to support audits, cybersecurity reviews, or internal reporting requirements.
Platform & Technology
• Software Management via IT PROTECT: Our system leverages the advanced capabilities of our Remote Monitoring and Management agent to deliver highly configurable, reliable patch management. Our automated system patching solution enhances precision and flexibility, offering smarter scheduling, retry logic, and update exclusions where needed.
• Supported Systems: We primarily support patching for Windows-based operating systems. Patching support for third-party applications may not be available for all software and is subject to compatibility and licensing.
• MacOS & app store software updates. MacOS devices are managed differently than Windows devices. Apple mandates and restrictions to the operating system produce limitations outside our control when automating the process of updating the OS. We configure each managed MacOS endpoint for automated updating of MacOS and supported app store updates on the endpoint itself. These are not automatically deployed by Cloud Matrix IT or a third party provider. Updates are applied by the system via the system updates feature within MacOS, which has some manual processes.
Client Responsibilities & Limitations
• Device Availability: Systems must be online and reachable by our remote monitoring and management (RMM) platform during scheduled patching windows to receive updates. Devices that are offline may fall behind in patch compliance.
• Reboot After Updates: Users are expected to promptly reboot their machines when they receive a reboot notification following a system update. Failure to reboot may prevent future updates from being downloaded and installed, leading to potential security vulnerabilities and system instability.
• Change Management: Clients must notify Cloud Matrix IT of any critical applications or business processes that require exclusions or special handling during patching cycles. This helps avoid interruptions to essential workflows.
• Third Party Application Patching: Our patching service covers operating system updates. Third-party application patching (e.g., Adobe, Java, Chrome) may be included but are not guaranteed.
• No Guarantee Against Zero-Day Threats: While automated patching significantly reduces vulnerability windows, no patching solution can protect against every zero-day exploit. Clients are encouraged to maintain layered security strategies including endpoint protection and threat detection. Deployment Profiles & Timeframes. A deployment profile may be configured for your Microsoft Windows operating systems that will include, at our discretion, how your machines will receive updates and when those will be deployed. It is the responsibility of the client to maintain an active connection to the internet for their machines to receive and process updates. We do not warrant or guarantee that any Update will get applied if machines are not on and connected to the internet. It is also the responsibility of the client to regularly reboot their machine after updates have been applied. Not doing so may cause performance or other security related issues.
Cybersecurity Awareness Training
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides Advanced Cybersecurity Awareness Training to help protect your organization from human-targeted cyber threats. This training is a critical component of your overall security strategy, empowering employees to recognize, avoid, and report phishing attacks, social engineering tactics, and other common cyber risks.
Service Scope
• Ongoing Training Campaigns: We deliver recurring, bite-sized cybersecurity training modules tailored to your organization’s needs and employee roles. Training content is engaging, easy to digest, and designed to build awareness without overwhelming users.
• Simulated Phishing Attacks: We launch periodic simulated phishing emails to assess your team’s readiness and reinforce key security behaviors in a safe environment. These simulations mimic real-world attack tactics without risking any actual compromise.
• User Performance Tracking: We monitor participation, phishing test results, and training completion rates. Reports are shared with key stakeholders to identify areas of improvement and track overall organizational risk posture over time.
• Customizable Content: Training modules may be customized by industry, department, or threat type to ensure relevance and alignment with your internal policies or compliance frameworks (e.g., HIPAA, PCI, etc.).
User Engagement & Expectations
• Required Participation: All users enrolled in the program are expected to complete assigned training modules within the designated timeframes. Consistent participation is essential to the effectiveness of the program.
• Phishing Simulation Response: Users should treat simulated phishing emails as they would a real threat—by avoiding clicks on suspicious links or attachments and reporting the email using your designated reporting method.
• No Penalty for Mistakes: Training and simulations are educational tools, not disciplinary actions. The goal is to help users improve their awareness and response, not to punish mistakes.
Client Responsibilities & Limitations
• User Enrollment & Offboarding: Clients are responsible for providing an up-to-date list of users to be enrolled in the training program and notifying Cloud Matrix IT of any staffing changes to ensure accurate participation.
• Internal Communication: Clients should communicate the importance of cybersecurity awareness training to their teams and encourage participation as part of a company-wide culture of security.
• Awareness Is Not a Guarantee: While training greatly reduces the risk of human error, no training program can guarantee complete prevention of phishing or social engineering success. Training should be paired with technical controls like email filtering, MFA, and endpoint protection.
By investing in ongoing cybersecurity awareness training through Cloud Matrix IT and BullPhish ID, your organization takes an essential step in reducing human-related vulnerabilities and strengthening its overall security posture.
Please see Anti-Virus; Anti-Malware and Breach / Cyber Security Incident Recovery sections below for important details.
Advanced Email Security & Filtering
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides advanced email security protection through a third party, that is an AI-driven email security platform designed to detect, prevent, and respond to phishing, business email compromise (BEC), and other email-borne threats.
· Managed email protection from phishing, business email compromise (BEC), SPAM, and email-based malware.
· Friendly Name filters to protect against social engineering impersonation attacks on managed devices.
· Protection against social engineering attacks like whaling, CEO fraud, business email compromise or W-2 fraud.
· Protects against newly registered and newly observed domains to catch the first email from a newly registered domain.
· Protects against display name spoofing.
· Protects against “looks like” and “sounds like” versions of domain names.
Service Scope
• Deployment & Configuration: We manage the deployment and configuration of our advanced email security solution within your Microsoft 365 or Google Workspace environment. This includes initial setup, email routing adjustments, and integration with your existing email infrastructure.
• AI-Driven Threat Protection: Our advanced email security solution leverages artificial intelligence to continuously analyze email traffic and detect suspicious or malicious messages. Features include:
o EmployeeShield® – Alerts users to suspicious emails directly in their inbox, allowing them to verify or report threats.
o Phish911™ – Enables users to easily report phishing attempts with a single click, triggering automated containment.
o TrustGraph® – Builds a trust network to identify abnormal communications based on sender behavior, content, and historical patterns.
• Monitoring & Incident Response: Cloud Matrix IT monitors alerts and threat reports. When malicious emails are detected, we provide response support, including threat analysis and assistance with containment actions if needed.
• User Awareness Support: We assist in educating users on recognizing and responding to email threats using insights and best practice guidance.
Data Access & Limitations
• Email Content Review: While our advanced email security solution inspects email content to identify threats, Cloud Matrix IT does not read or access user email content beyond what is necessary for threat detection and incident response. Any email analysis is limited to security-related investigations or user requests.
• End-User Engagement: End-users play a key role in this solution. Timely reporting of suspicious messages via Phish911™ and attention to EmployeeShield® warnings are essential for maximizing protection.
• No Control Over Message Delivery Outside Scope: Our advanced email security solution operates as an additional layer of protection and is not a replacement for your core email filtering system. While highly effective, no email security solution can guarantee 100% threat prevention.
• Client Responsibility: Clients are responsible for maintaining security awareness within their organization, promptly notifying Cloud Matrix IT of any suspicious email activity, and ensuring all users are enrolled and engaged with the platform’s features.
User Responsibility & Engagement
The effectiveness of our advanced email security solution depends not only on its AI-driven threat detection, but also on active user participation. Your employees play a critical role in maintaining the accuracy of email classification and preventing legitimate messages from being misidentified as threats.
• Using EmployeeShield®: Users must review and respond to the EmployeeShield® banner that appears on emails flagged as potentially suspicious. When prompted, users should either report the email as phishing or confirm it as safe. This feedback helps train the system and improves future accuracy.
• Consequences of Inaction or Incorrect Handling: If suspicious emails are not properly reported or verified by the user:
o Legitimate emails may be incorrectly classified as phishing.
o Emails may be automatically quarantined, moved to spam, or deleted.
o False positives may increase, disrupting normal business communication.
Proper and consistent use of these tools is essential to maintaining a secure and productive email environment. By using our advanced email security solution, your organization benefits from intelligent, automated email threat protection, while maintaining full control over email communications and internal security practices.
Please see Anti-Virus; Anti-Malware and Breach / Cyber Security Incident Recovery sections below for important details.
Microsoft Azure Virtual Machine Backup/Storage
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides reliable backup and recovery services for Virtual Machines (VMs) hosted in Microsoft Azure environments. Leveraging Azure Backup, we help ensure that your cloud-based infrastructure is protected from data loss, accidental deletion, or system failure.
The Azure Backup service provides simple, secure, and cost-effective solutions to back up your data and recover it from the Microsoft Azure cloud. Azure Backup provides independent and isolated backups to guard against unintended destruction of the data on your VM(s) or other Azure services. Backups are stored in a Recovery Services vault with built-in management of recovery points. Configuration and scaling are simple, backups are optimized and can easily be restored as needed. As part of the backup process, a snapshot is taken, and the data is transferred to the Recovery Services vault with no impact on production workloads. The snapshot provides different levels of consistency.
Costs: Azure Backup costs vary depending on the amount of data being backed up.
Size: The size can fluctuate as so can the costs. This service will require a monthly Azure Subscription that will be maintained by Cloud Matrix IT.
Retention: Standard retention policy period for Azure virtual machines are 30 days.
Service Scope
• VM Provisioning & Configuration: We provision and manage Azure Virtual Machines within your tenant, customized to meet your operational and performance needs.
• Backup Enablement: As part of our VM deployment or ongoing management, we configure and maintain Azure Backup for each Virtual Machine. This includes:
o Creating and assigning backup policies.
o Scheduling daily backups with defined retention periods.
o Storing recovery points in Azure Recovery Services Vaults.
• Monitoring & Management: Cloud Matrix IT monitors backup jobs and alerts for failures or inconsistencies. We take corrective action as needed to ensure backup integrity and continuity.
• Recovery Support: In the event of accidental data loss or system failure, we support the restoration of full VMs or individual files (when supported), coordinating recovery efforts with your internal teams to minimize downtime.
Data Access & Retention
• Client Data Ownership: You retain full ownership and control of your data and Azure environment. All backups are stored within an Cloud Matrix IT Azure subscription assigned to your tenant. The subscription is managed by Cloud Matrix IT and our third-party providers.
• Retention Policies: Backup retention is configured according to the policy agreed upon during onboarding (generally 30 days). Clients may request changes to frequency or retention settings to align with business or compliance requirements in writing by mail or email to Cloud Matrix IT.
• Storage Costs: Backup storage is consumed within your Azure environment. Clients are responsible for associated storage costs, which may vary based on backup frequency, retention settings, and data volume.
Limitations & Client Responsibilities
• No Guarantee of Zero Data Loss: While Azure Backup is a highly reliable solution, no backup service can guarantee absolute protection. Regular testing of recovery points is recommended and testing is provide by Cloud Matrix IT on a regular basis.
• Client Notification: Clients are responsible for notifying Cloud Matrix IT of changes to VM usage, critical data locations, or business continuity needs that may impact backup requirements.
Scope of Protection: Azure Backup covers the Virtual Machine and its data at the time of backup. It does not include backups of workloads or services outside the VM unless otherwise specified.
Microsoft Azure Virtual Desktop (AVD) Services
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides secure, scalable, and fully managed Azure Virtual Desktop (AVD) solutions that enable your team to access cloud-hosted Virtual Machines from anywhere, on any device. AVD delivers a modern remote desktop experience backed by Microsoft’s Azure infrastructure and our expert configuration and support.
Azure Virtual Desktop (AVD) is a cloud-based service that allows you to access virtual desktop and applications from anywhere and from most devices. It is designed for Microsoft 365 customers who want to leverage the power and security of the cloud for their remote work needs. You must have an M365 tenant that we can deploy AVD to. The hardware on which AVD operates is solely managed by Microsoft, Cloud Matrix IT only manages the software environment, i.e. desktop environment, which will be used by the user.
This service is provided and invoiced on a monthly subscription basis managed by Cloud Matrix IT and pricing can fluctuate depending on usage.
Services Provided
We can develop, configure, and manage the Azure Virtual Desktop environment, via an Azure subscription through our Microsoft provider to you, the Client, that may include:
· Creating and deploying AVD or virtual machines (VMs) on Azure
· Assigning users and groups to access your AVD or VMs
· Installing and updating applications on your AVD or VMs
· Monitoring and optimizing the performance and availability of AVD or your VMs
· Securing and backing up your data on Azure
· Providing technical support and troubleshooting
Service Scope
• Environment Design & Deployment: We design and deploy AVD environments tailored to your organization’s needs, including:
o Host pool creation and configuration
o User profile management
o Network and security policy integration
o Application publishing and desktop assignments
• User Access to Azure VMs: Through AVD, users securely connect to Windows desktops and applications running on Azure Virtual Machines. Each session is delivered with the performance and experience of a local machine, while all data and processing remain in the cloud.
• Identity & Security Integration: We integrate AVD with Microsoft Entra ID and your existing security policies to support Single Sign-On (SSO), Multi-Factor Authentication (MFA), and conditional access controls.
• Ongoing Management & Support: Cloud Matrix IT manages session host performance, updates, scaling, and resource optimization. We monitor the environment to ensure availability, security, and responsiveness.
User Experience
• Anywhere Access: Users can securely access their virtual desktops from Windows, macOS, iOS, Android, or any HTML5-compatible browser.
• Consistent Experience: Each user receives a consistent desktop experience, including access to company applications, files, and network resources.
• Optimized for Microsoft 365: AVD is optimized for Microsoft Teams, OneDrive, and Office applications for seamless productivity.
Client Responsibilities & Limitations
• Licensing Requirements: Clients must maintain appropriate Microsoft licenses for AVD use (e.g., Microsoft 365 Business Premium, E3/E5, or Windows 10/11 Enterprise). Cloud Matrix IT can assist in verifying licensing requirements.
• User Management: While we assist in provisioning and onboarding users, clients are responsible for notifying us of any changes to user access needs, role adjustments, or employee offboarding.
• Data Handling: All data accessed through AVD is stored within the client’s Azure environment. Clients retain full control and ownership of their data and are responsible for internal data governance and compliance.
By utilizing Azure Virtual Desktop, your organization gains secure, flexible access to enterprise-grade computing resources—fully managed by Cloud Matrix IT and optimized for remote work and hybrid environments.
Microsoft Azure Virtual Machines
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides design, provisioning, and management of Azure Virtual Machines (VMs) within your organization’s Microsoft Azure environment. Whether supporting infrastructure workloads, line-of-business applications, or cloud-hosted desktops, our team ensures your VMs are secure, optimized, and built to scale with your business.
This service is provided and invoiced on a monthly subscription basis managed by Cloud Matrix IT and pricing can fluctuate depending on usage.
Service Scope
• VM Planning & Design: We assess your organization’s needs to determine the appropriate VM sizes, operating systems, and storage configurations. This includes evaluating CPU, RAM, disk IOPS, and networking requirements based on your intended workload.
• Provisioning & Deployment: We create and deploy Azure VMs within your existing Azure tenant, or as part of a new environment buildout. This includes:
o Resource group configuration
o Virtual network and subnet setup
o Public IP and network security group (NSG) configuration
o VM naming conventions and tagging for manageability
• Security & Access Configuration: We configure secure access to VMs using Microsoft Entra ID (formerly Azure AD), local administrator policies, and best-practice remote access protocols (e.g., RDP or Bastion). Multi-factor authentication (MFA) is enforced wherever applicable.
• Ongoing Support & Optimization: Cloud Matrix IT provides ongoing VM management, including performance monitoring, system updates (via our automated patching service), backup configuration, and resource scaling recommendations.
• Virtual Machine Backup/Restore: All Virtual Machines will include Azure backup and restore services with any VM deployed and/or managed by Cloud Matrix IT. Please see “Microsoft Azure Virtual Machine Backup/Storage” solution above.
Managed Security for Virtual Machines
In addition to the native Azure security controls provided by Microsoft, all Azure Virtual Machines managed by Cloud Matrix IT are protected by our IT PROTECT platform.
• Endpoint Detection & Response (EDR): All VMs are equipped with advanced EDR technology that continuously monitors for suspicious behavior, unauthorized access attempts, and indicators of compromise. EDR provides deep visibility into endpoint activity and supports rapid threat detection and response.
• Managed Detection & Response (MDR): Our 24/7/365 Security Operations Center+ (SOC+) monitors your VMs for threats in real-time. When suspicious activity is detected, our team investigates, triages, and responds swiftly to contain threats before they can escalate.
• Proactive Threat Prevention: Our IT PROTECT platform also includes threat intelligence, behavioral analytics, and automated remediation capabilities to reduce risk and prevent security incidents.
• Security Hardening: As part of the deployment, we apply baseline security configurations and best practices to each VM, including account controls, audit logging, and system hardening aligned with industry standards.
With Cloud Matrix IT managing both your Azure infrastructure and endpoint protection, your virtual machines benefit from a multi-layered defense strategy that addresses both platform-level and workload-specific threats.
Client Responsibilities & Limitations
• Azure Subscription Ownership: While all resources are deployed within the client’s Azure environment, Cloud Matrix IT manages the subscription through our distributor where the VM/AVD will be billed. Clients are responsible for the associated consumption costs billed directly by Cloud Matrix IT.
• Workload-Specific Software: Clients must provide and manage any line-of-business or third-party applications installed on the VMs, unless otherwise specified in a managed service agreement.
• Change Notification: Clients should notify Cloud Matrix IT of planned changes to workload requirements, licensing, or user access needs that may impact VM configuration or performance.
• Licensing: Operating system licensing is typically bundled with the Azure VM pricing model. Any specialty or third-party software must be licensed separately by the client.
• Managed Device: All virtual machines will be a managed device within the IT PROTECT platform. Client is responsible for all fees related to a managed device as outlined in the initial quote or under our master services agreement.
• Microsoft Licensing: It is required to have an eligible Microsoft 365 Business Premium license to use Azure Virtual Machines via AVD.
• Azure Policies: You are responsible for complying with the applicable laws and regulations regarding the use of Azure Virtual Machines.
• Virtual Machine Local Content: Virtual Machines are like any other Windows device in that you can store documents etc. on the device. You are responsible for any content or data that you store or transmit using Azure Virtual Machines.
By leveraging Azure Virtual Machines through Cloud Matrix IT, your organization gains scalable, secure infrastructure built for the cloud—designed, deployed, and maintained by a trusted technology partner.
Business Continuity & Disaster Recovery (Onsite physical backup solution)
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience. All data transmitted over the Internet may be subject to malware and computer contaminants such as viruses, worms and trojan horses, as well as attempts by unauthorized users, such as hackers, to access or damage Client’s data. Neither Cloud Matrix IT nor its designated affiliates will be responsible for the outcome or results of such activities.
BDR services require a reliable, always-connected internet solution. Data backup and recovery time will depend on the speed and reliability of your internet connection. Internet and telecommunications outages will prevent the BDR services from operating correctly. In addition, all computer hardware is prone to failure due to equipment malfunction, telecommunication-related issues, etc., for which we will be held harmless. Due to technology limitations, all computer hardware, including communications equipment, network servers and related equipment, has an error transaction rate that can be minimized, but not eliminated.
Cloud Matrix IT cannot and does not warrant that data corruption or loss will be avoided, and Client agrees that Cloud Matrix IT shall be held harmless if such data corruption or loss occurs. Client is strongly advised to keep a local backup of all stored data to mitigate against the unintentional loss of data.
• 24/7 monitoring of backup system, including offsite backup, offsite replication, and an onsite backup appliance (“Backup Appliance”).
• Troubleshooting and remediation of failed backup disks.
• Preventive maintenance and management of imaging software.
• Firmware and software updates of backup appliance.
• Problem analysis by the network operations team.
• Monitoring of backup successes and failures.
• Daily recovery verification.
Backup Data Security: All backed up data is encrypted in transit and at rest in 256-bit AES encryption. All facilities housing backed up data implement physical security controls and logs, including security cameras, and have multiple internet connections with failover capabilities.
Backup Retention: Backed up data will be retained for a minimum of one (1) year, or at our discretion.
Backup Alerts: Managed servers will be configured to inform of any backup failures.
Recovery of Data: If you need to recover any of your backed up data, then the following procedures will apply:
• Service Hours: Backed up data can be requested during our normal business hours, which are currently Monday through Friday, 8 a.m. to 5 p.m. not including federal holidays. Off hours’ time sensitive requests are actioned on a case by case basis.
• Request Method. Requests to restore backed up data should be made through one of the following methods:
o Email: support@cloudmatrixit.com
o Web portal: Client ticketing portal
o Telephone: 414-519-5738
• Restoration Time: We will endeavor to restore backed up data as quickly as possible following our receipt of a request to do so; however, in all cases data restoration services are subject to technician availability. Generally, we can restore between 0 and 100MB of data within 4 hours of your request, and 100 MB to 500 MB within 8 hours of your request. Data restoration exceeding 500 MB will be handled in accordance with technician availability. Time to restore can depend on many factors and times are not guaranteed.
Cloud Backup for Microsoft 365 & Google Workspace
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides automated daily backups for Microsoft 365 and Google Workspace environments to protect critical business data and enable reliable recovery in the event of accidental deletion, data corruption, or cyber incidents. This service ensures comprehensive protection of cloud-based productivity and collaboration platforms through a fully managed and secure backup solution.
All data transmitted over the Internet may be subject to malware and computer contaminants such as viruses, worms and trojan horses, as well as attempts by unauthorized users, such as hackers, to access or damage Client’s data. Neither Cloud Matrix IT nor its designated affiliates will be responsible for the outcome or results of such activities.
This service requires a reliable, always-connected internet solution. Data backup and recovery time will depend on the speed and reliability of your internet connection. Internet and telecommunications outages will prevent the BDR services from operating correctly. In addition, all computer hardware is prone to failure due to equipment malfunction, telecommunication-related issues, etc., for which we will be held harmless. Due to technology limitations, all computer hardware, including communications equipment, network servers and related equipment, has an error transaction rate that can be minimized, but not eliminated. Cloud Matrix IT cannot and does not warrant that data corruption or loss will be avoided, and Client agrees that Cloud Matrix IT shall be held harmless if such data corruption or loss occurs. It is as the Clients discretion to keep a local backup of all stored data to mitigate against the unintentional loss of data.
What’s Backed Up
We back up the following core services on a daily basis:
• Microsoft 365:
o Exchange Online (Email)
o OneDrive for Business
o SharePoint Online
o Teams Chats & Channels
o Outlook Calendars & Contacts
• Google Workspace:
o Gmail
o Google Drive (including My Drive and Shared Drives)
o Google Calendar
o Google Contacts
Data Security
• Encryption: All data is encrypted both in transit and at rest using industry-standard encryption protocols to ensure the highest level of data security and compliance.
• Access Control: Backup access is restricted to authorized Cloud Matrix IT personnel. Clients do not have direct access to backup storage but may request data restoration at any time.
• Secure Storage: Backed-up data is stored in a secure, geographically redundant cloud infrastructure, ensuring high availability and resilience.
Retention Policy
• Daily Backups: Backups occur once daily and are retained according to our default policy (e.g., up to 365 days or longer depending on service tier).
• Custom Retention: Backed up data will be retained for a minimum of one (1) year, or at our discretion. Extended retention periods can be configured based on specific regulatory or business requirements, subject to additional storage usage.
• Storage Overage: Clients are responsible for any storage overages incurred as a result of excessive data volumes beyond the included backup allocation. Cloud Matrix IT will notify clients if they are approaching or exceeding their allocated limits. For clients who have a pooled storage across all Microsoft 365 or Google Workspace Tenants that exceed an average of 100GB per License for a period of two (2) consecutive months or more, may incur additional fees for overage storage requirements or a lesser retention policy for housing the backup data.
Alerts & Monitoring
• Automated Monitoring: Backup jobs are monitored daily by Cloud Matrix IT for failures or anomalies.
• Failure Notifications: In the event of backup failure or issue, our team is alerted and will investigate promptly to ensure your data is protected without interruption.
• Client Alerts: We may notify clients of persistent issues or errors related to specific user accounts or services that require client action.
Data Recovery & Restoration
If you need to recover any of your backed-up data, the following procedures apply:
• Service Hours: Data recovery requests are handled during normal business hours:
Monday through Friday, 8 a.m. to 5 p.m. Central Time, excluding federal holidays.
After-hours time-sensitive requests will be addressed on a case-by-case basis depending on technician availability.
• Request Methods: You can request a restore using any of the following:
o Email: support@cloudmatrixit.com
o Web Portal: Client ticketing portal
o Phone: 414-519-5738
• Estimated Recovery Time:
o Up to 100MB: Typically restored within 4 business hours
o 100MB – 500MB: Typically restored within 8 business hours
o Over 500MB: Restored as soon as technician availability allows
Please note: Restoration times are subject to data volume, complexity, and system load at the time of request. While we aim to respond quickly, timeframes are not guaranteed.
By utilizing Cloud Matrix IT’s Automated Cloud Backup solution, your organization gains peace of mind knowing that your cloud-based email, files, calendars, and collaboration data are safely backed up and recoverable in the event of loss—without relying solely on Microsoft or Google’s limited built-in recovery options.
Dark Web Monitoring & Response
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides Dark Web Monitoring & Response as part of our IT PROTECT cybersecurity platform. This service proactively monitors the dark web for compromised credentials and sensitive data tied to your organization—helping to identify breaches before they result in serious damage.
Using enterprise-grade threat intelligence technology we continuously scan and analyze criminal marketplaces, data dumps, and hidden forums for exposed usernames, passwords, and other personal or business-related information.
Why It Matters
• Early Detection: Identifying compromised data before it’s used in an attack gives your organization a critical head start to contain the risk.
• Security Awareness: Knowing what’s been exposed helps you make informed decisions about credential hygiene, MFA enforcement, and employee training.
• Regulatory Alignment: Dark web monitoring supports cybersecurity best practices and may contribute to compliance with frameworks like HIPAA, PCI-DSS, or NIST.
Service Scope
• Credential Monitoring: We continuously monitor for exposed credentials associated with your organization’s domains and email addresses.
• Automated Alerts: If compromised data is found, our system generates real-time alerts, allowing us to respond quickly to reduce your exposure to cybercriminal activity.
• Human-Verified Threat Intelligence: Alerts are verified for accuracy and relevance before being escalated, reducing false positives and ensuring actionable intelligence.
• Incident Response Support: When a credential compromise is detected, Cloud Matrix IT assists in identifying affected accounts and guiding secure password resets or other mitigation steps.
Data Coverage
We monitor the following types of data commonly sold or traded on the dark web:
• Email addresses and usernames
• Passwords (plaintext or hashed)
• IP addresses and device identifiers
• Account credentials tied to cloud services, banking, or business systems
• Leaked information tied to past data breaches
Client Responsibilities & Limitations
• Credential Exposure Is External: Dark web data breaches usually originate from third-party services (e.g., social media, SaaS platforms, vendor breaches). This monitoring service is designed to detect exposure—not prevent the original breach.
• Prompt Action Required: Clients are expected to act promptly when notified of a compromise. This may include updating passwords, enabling MFA, or adjusting internal access controls. We work with you to mitigate these exposures.
• No Removal of Data from the Dark Web: Once credentials are leaked or sold, they cannot be deleted from the dark web. Our service provides visibility and response, not removal.
• Limited to Domain Scope: Monitoring is limited to email addresses and accounts associated with your organization’s verified domains and approved user list.
By integrating Dark Web Monitoring & Response into your IT PROTECT stack, Cloud Matrix IT helps your organization stay vigilant against evolving cyber threats—before attackers strike.
Dedicated Email Security Consultant
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
As part of our commitment to protecting your organization from evolving email threats, Cloud Matrix IT offers access to a Dedicated Email Security Consultant. This expert works directly with your team to enhance your defenses, improve user awareness, and ensure best practices are implemented across your organization.
Service Scope
• Personalized Security Guidance: Our consultants assess your current email security posture and provide tailored recommendations aligned with your industry, threat landscape, and internal policies.
• Training & Awareness: We provide employee education and leadership training on recognizing phishing attempts, handling suspicious emails, and using security tools like banners and reporting features effectively.
• Policy Review & Optimization: We assist in refining your email filtering rules, phishing simulations, and domain protection strategies (e.g., SPF, DKIM, DMARC) to ensure a layered defense. Some suggestions may be out of scope and may be billed on a T&M basis.
• Ongoing Strategy & Support: Your consultant is available for periodic reviews, strategy updates, and incident response support, helping your business stay ahead of emerging threats.
With a Dedicated Email Security Consultant from Cloud Matrix IT, your organization benefits from specialized expertise focused on securing one of the most targeted and vulnerable areas of your digital environment—email.
Device Management, Monitoring, & Alerting
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Software agents installed in Covered Equipment (defined below) report status and IT-related events on a 24x7 basis; alerts are generated and responded to in accordance with the Service Levels described below.
• Includes capacity monitoring, alerting us to severely decreased or low disk capacity (covers standard fixed HDD partitions, not external devices such as USB or mapped drives)
• Includes routine operating system inspection and cleansing to help ensure that disk space is increased before space-related issues occur.
• Review and installation of updates and patches for supported software.
• Online status monitoring, alerting us to potential failures or outages.
• Performance monitoring, alerting us to unusual processor or memory usage.
• Endpoint protection agent monitoring, alerting us to potential security vulnerabilities.
• Routine operating system inspection and cleansing.
• Secure remote connectivity to the endpoint and collaborative screen sharing.
• Asset inventory and workstation information collection.
In addition to the above, our remote monitoring and management service will be provided as follows:
Event Server Workstation
Hardware Failures Yes No
Device Offline Yes Yes
Failed/Missing Updates Yes Yes
Low Disk Space Yes Yes
Agent missing/misconfigured Yes Yes
Excessive Uptime Yes Yes
Automatic Reboots (weekly) No Yes
Email Phish911 Reporting
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides clients with a built-in Phish Reporting Button within Microsoft Outlook, enabling users to quickly and easily report suspicious emails. This feature is a vital part of your email security strategy, allowing your team to assist in identifying threats and preventing further spread across your organization.
Service Scope
• One-Click Reporting: The button is conveniently embedded within the Outlook interface (desktop, web, and mobile) so users can report suspicious emails with a single click.
• Real-Time Threat Escalation: Reported emails are automatically flagged and forwarded to Cloud Matrix IT’s security team for review and investigation. When necessary, we take action to contain the threat and notify affected users or systems.
• Improved Threat Intelligence: Each report contributes to your organization’s threat intelligence by helping refine filters, train AI-driven tools (like Graphus), and improve future threat detection.
• User Empowerment: Empowering users to report phishing attempts reinforces a culture of shared cybersecurity responsibility and makes them an active part of your defense strategy.
Client Responsibilities
• User Training: Clients should encourage all users to report suspicious messages and provide periodic reminders on how and when to use the Phish Reporting Button.
• Timely Reporting: The sooner a threat is reported, the faster it can be investigated and mitigated. Prompt action helps limit the potential spread of phishing campaigns across your environment.
• Not a Replacement for Filtering: While powerful, the reporting tool supplements existing email security solutions and is not a substitute for advanced email threat protection.
By leveraging the Email Phish Reporting Button, your organization gains faster visibility into targeted threats and enhances the effectiveness of your email security platform with valuable, user-driven intelligence.
Employee Home Network Assistance
Cloud Matrix IT is offering a one-time consulting session with each of your employees who utilize a managed endpoint. If they're experiencing issues while using their device to do their job at home, we can discuss various possibilities and make suggestions to help them solve that issue.
Please note: Because Cloud Matrix IT does not own or manage these networks, we are not liable for any damages or losses that may arise from our consulting services or best practice suggestions to your employees, such as data breaches, service interruptions, or noncompliance issues. We also advise that you follow best practices and guidelines.
Employee Productivity Monitoring
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Employee Monitoring & Productivity Insights
Cloud Matrix IT provides optional employee monitoring features through our employee productivity monitoring solution. This includes visibility into workstation activity, application usage, login times, and idle durations to help businesses understand employee workflows and identify potential productivity or security concerns.
Depending on the request from the client, T&M charges may apply at the then current development rates.
Capabilities may include:
• Real-time user activity monitoring (keyboard/mouse activity)
• Application and website usage tracking
• Time-on-task analysis and idle time reporting
• Workstation login/logout reports
• Optional screenshot capture (optional add-on)
• User productivity scoring (optional add-on)
Privacy & Transparency:
Monitoring is configurable based on your company's HR and legal policies. We recommend clients notify employees of all monitoring activities. Reports are only accessible to authorized client contacts and are not used by Cloud Matrix IT for disciplinary purposes.
1. Scope of Services
(a) At Client’s request, Provider may facilitate implementation and configuration of Monitoring Services via the Third-Party Provider.
(b) Monitoring Services may include, without limitation:
• Workstation activity tracking (keyboard/mouse activity)
• Application and website usage tracking
• Time-on-task and idle time reporting
• Workstation login/logout records
• Optional screenshot capture and productivity scoring (available add-ons)
(c) Provider does not actively monitor or review Client’s employees, and shall not interpret, enforce, or ensure compliance with any Client human resources, labor, or workplace policies.
(d) All features, functionality, and retention periods are governed by the Third-Party Provider’s then-current terms and policies, which may change without notice.
As part of the Employee Productivity Monitoring service, Cloud Matrix IT (“Provider”) will perform the following activities in connection with the Third-Party Provider’s platform:
1. Portal Setup & Configuration
o Establish and configure the monitoring portal in accordance with Client’s specifications and the capabilities of the Third-Party Provider’s system.
o Apply standard security settings and access controls based on Client’s designated administrator list.
2. Agent Deployment
o Provide deployment & installation for the monitoring agent to Client-approved managed endpoints.
o Verify agent connectivity to the monitoring portal.
3. Ongoing Maintenance
o Perform routine maintenance to ensure the monitoring platform is operating within normal parameters.
o Apply updates and patches to the monitoring agent or portal configuration as released by the Third-Party Provider.
4. Upgrades & Feature Enablement
o Facilitate the activation of newly available features upon Client request and subject to applicable licensing or fees.
o Advise Client on compatibility or prerequisites for new features.
5. Reporting Assistance
o Provide guidance on accessing and generating standard monitoring reports.
o Assist Client administrators with interpreting platform functions and report filters (without providing legal or HR policy interpretation).
2. Client Responsibilities
(a) Client shall be solely responsible for:
• Determining the scope, configuration, and permitted use of Monitoring Services.
• Ensuring such use complies with all applicable laws, including labor, privacy, and union-related requirements.
• Providing prior written notice to, and obtaining any required consent from, all employees or individuals whose activity will be monitored.
(b) Client shall designate in writing the personnel authorized to access monitoring reports and data.
(c) Monitoring Services may not be activated until all required employee notifications and consents have been completed by Client.
3. Data Ownership and Handling
(a) All monitoring data generated shall be deemed “Client Data” and owned exclusively by Client.
(b) Provider does not review, audit, or verify the accuracy, completeness, or legality of any monitoring data.
(c) Data retention is in accordance with the Third-Party Provider’s current retention policy (currently six (6) months for the Essentials plan).
(d) Upon termination, all monitoring data will be permanently deleted unless Client submits a written retrieval request before termination. Data deletion is irreversible.
4. License Model
(a) Services are licensed on a per-user basis, with a minimum of five (5) paid licenses required at all times.
(b) Licenses are user-based (not device-based) and consumption is determined in accordance with the Third-Party Provider’s usage rules.
(c) Licenses may not be reduced to below the initial purchase quantity during the term.
5. License Usage and Management
(a) Licenses are consumed when a user agent collects or stores data for a unique user, even if the user is no longer actively monitored, until all historical data is permanently deleted.
(b) Clients are responsible for managing licenses, merging duplicate user records, and deleting unused historical data.
(c) When license counts exceed the purchased amount, the Third-Party Provider’s enforcement policies apply.
6. Limitations of Liability
(a) Provider shall not be liable for:
(i) Downtime, service interruptions, feature changes, or security incidents attributable to the Third-Party Provider.
(ii) Inaccuracies, omissions, or delays in monitoring data.
(iii) Any Client decisions, actions, or omissions based on monitoring data, including disciplinary or termination actions.
(b) Provider makes no representation or warranty regarding the legality of Monitoring Services in any jurisdiction.
7. Term and Termination
(a) Unless otherwise agreed in writing, the Monitoring Services term is twelve (12) months.
(b) Provider may suspend or terminate Monitoring Services for nonpayment or as required by the Third-Party Provider’s terms.
(c) The Third-Party Provider may modify, suspend, or discontinue any feature at any time without liability to Provider.
Endpoint Detection & Response (EDR)
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
As part of our IT PROTECT cybersecurity platform, Cloud Matrix IT delivers advanced Endpoint Detection & Response (EDR) to protect your organization's devices against modern threats. Powered by industry-leading Advanced AI technology under the hood, this fully managed solution provides real-time threat detection, prevention, and response across your endpoints—without requiring constant user intervention.
Service Scope
• Behavior-Based Threat Detection: Our EDR solution continuously monitors endpoint activity to detect malicious behavior, including ransomware, zero-day exploits, fileless attacks, and lateral movement—far beyond what traditional antivirus can see.
• Automated Response & Containment: When a threat is detected, the system can automatically kill malicious processes, quarantine affected files, and isolate devices from the network to prevent further spread.
• Active Threat Hunting: Our security team reviews suspicious activity and investigates alerts, ensuring no critical events go unnoticed. We proactively respond to incidents and notify you of confirmed threats.
• Rollback Capabilities (Where Supported): On supported systems, our EDR solution includes rollback functionality to restore files and system settings to a pre-infection state, minimizing downtime and data loss.
Data Visibility & Control
• Real-Time Alerts & Reporting: Clients receive notifications of confirmed threats along with relevant details, actions taken, and recommendations if further steps are needed.
• Device Inventory & Status Monitoring: Our platform provides visibility into your entire endpoint fleet, showing the health, status, and protection level of each device under management.
Client Responsibilities & Limitations
• Device Availability: Devices must remain online and connected to the internet or corporate network to receive full real-time protection, updates, and reporting.
• End-User Security Awareness: While our EDR provides strong protection, it should be used alongside other security measures, including user training, email filtering, and access controls.
• Not a Substitute for Full Backups: Although some rollback capabilities exist, the EDR platform is not a replacement for comprehensive backup solutions. Clients should continue to maintain secure data backups and disaster recovery procedures.
With Cloud Matrix IT’s Endpoint Detection & Response, your organization gains enterprise-grade security, fully managed by our expert team—offering a powerful defense against today’s most sophisticated endpoint threats.
Please see Anti-Virus; Anti-Malware and Breach / Cyber Security Incident Recovery sections below for important details.
Fully Managed SOC+ Cybersecurity Platform
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT delivers comprehensive, enterprise-grade protection for every managed endpoint through our IT PROTECT MDR+ Platform, powered by industry-leading technology. More than just MDR, our solution includes continuous 24/7/365 monitoring, real-time response, cloud environment protection, vulnerability management, and application control—designed to secure today’s hybrid businesses from endpoint to cloud.
24/7/365 Managed Detection & Response (MDR)+
When an attack occurs, speed is everything. Our MDR solution provides real-time threat detection, alerting, and human-led incident response—24/7/365.
• Our global Security Operations Center (SOC) actively monitors for signs of compromise, suspicious behavior, and advanced threats.
• Malicious activity is quickly contained and remediated, including the automatic isolation of compromised endpoints, the termination of malicious processes, and blocking lateral movement before it spreads.
• Threats are neutralized within minutes, minimizing damage and downtime while keeping your business operational.
Cloud Response
Our MDR+ platform extends protection into your cloud environment, offering continuous visibility and response across your Microsoft 365 and Google Workspace environments. Cloud Response helps reduce your cloud attack surface, detect unauthorized access or risky configurations, and respond immediately to threats in cloud services critical to your business.
Managed Endpoint Detection & Response (EDR)
We integrate our MDR+ platform with Cloud Matrix IT’s Endpoint Detection & Response (EDR) solution to deliver Managed EDR—a unified, streamlined defense strategy for all managed devices.
• Alerts are triaged and acted on by our cybersecurity specialists in real-time.
• Threats are remediated without waiting for user action.
• Our team ensures your devices stay protected with minimal disruption to users or operations.
Vulnerability Management
Gain insight into the security posture of your entire environment—internal, external, and cloud—from a centralized platform. We proactively scan for known vulnerabilities across systems, apps, and network endpoints, helping your team stay ahead of potential exploit paths before they are targeted.
• Regular vulnerability assessments
• Prioritized risk reporting
• Recommendations for remediation or mitigation
Application Control
Application Control empowers your business to maintain tight oversight of software usage while reducing friction for end users. Our managed team applies curated application policies based on real-world threat intelligence to:
• Block unauthorized or high-risk applications
• Minimize potential attack vectors
• Improve operational efficiency without sacrificing security
Always-On, Always-Secure
By deploying the IT PROTECT’s fully managed cybersecurity platform on every managed endpoint, Cloud Matrix IT provides clients with a comprehensive, always-on defense that goes far beyond standard cybersecurity tools. You benefit from:
• 24/7 human-led detection and response
• Cloud-integrated protection
• Full lifecycle endpoint protection
• Continuous visibility into vulnerabilities and application risks
This solution is fully managed by our expert team, allowing you to focus on growing your business while we handle the complex security operations.
Limitations & Client Responsibilities
To ensure the continued effectiveness and functionality of the IT PROTECT’s fully managed cybersecurity platform, the following conditions and client responsibilities must be met:
• Device Uptime & Connectivity: Endpoints must remain regularly connected to the internet and powered on during business hours to maintain real-time monitoring, threat detection, and policy enforcement. Devices that are offline or disconnected for extended periods could introduce risks in protecting your devices.
• Regular Reboots Required: Machines should be rebooted at least weekly to ensure proper operation of endpoint protection agents and to apply critical updates. Failing to reboot can lead to degraded security functionality and delayed threat detection or response.
• User Cooperation in Incident Response: In the event of a security incident, users may be asked to disconnect from the network, reboot their devices, or work with our team to mitigate the issue. Timely cooperation is essential to successful containment and remediation.
• Cloud Account Visibility: Cloud protection is limited to accounts and services integrated with our monitoring tools (e.g., Microsoft 365, Google Workspace). Clients are responsible for notifying Cloud Matrix IT of any new cloud applications or services that may require inclusion in the security scope.
• Unauthorized Software: Clients should avoid installing unapproved or unlicensed applications that may conflict with endpoint protection or increase exposure to risk. Application Control is enforced to reduce this risk.
• Scope of Service: While our MDR+ platform provides comprehensive protection, no security service can guarantee prevention of all threats. This service is most effective as part of a multi-layered security strategy, which includes secure backups, user awareness training, and proper access controls.
By adhering to these operational best practices, your organization ensures that our IT PROTECT fully managed cybersecurity platform performs at its highest level, delivering the rapid detection and response capabilities your business depends on.
Hardware Procurement Program
Cloud Matrix IT offers a convenient, low-risk Hardware Procurement Program designed exclusively for clients enrolled in our IT PROTECT platform. This program simplifies the process of acquiring secure, high-quality desktops and laptops tailored to your business needs—with the added benefit of a “test drive” period before purchase is finalized.
Device Selection & Test Drive
We work directly with you to evaluate your hardware needs and recommend appropriate options. All devices are selected in consultation with the client and are configured to support your business requirements.
Clients may test drive any device for up to 90 calendar days before purchase. If the device does not meet expectations, it may be returned within 80 days from the original shipment date, giving us time to coordinate return logistics with our hardware partner.
• No restocking fees apply for undamaged returns
• Devices must be in the condition it was sent with all original components
• Returns after 90 days are not accepted; the device is considered client-owned and billable
Ownership, Invoicing & Payment Terms
A signed quote is required for all hardware orders. Devices are not invoiced until the test period ends or the client confirms they wish to keep the device. Charges will appear on the client’s regular monthly invoice. Once a device is purchased, it becomes the property of the client.
Clients may also request hardware for non-managed users; however, these devices will not receive IT support or warranty services from Cloud Matrix IT. While we may extend the 90 day test drive to the client for these types of orders, the device must be purchased within that 90 day window.
Configuration & Delivery
All hardware purchased for the IT PROTECT platform is:
• Professionally configured by Cloud Matrix IT staff
• Pre-loaded with our IT PROTECT platform and security/management tools
• Customized to the needs of the client
• Shipped directly to the client or designated employee
Standard shipping costs are covered by Cloud Matrix IT. Return shipping (if applicable) is the responsibility of the client.
Warranty & Replacement
All devices purchased through our procurement program include a three (3) year warranty provided through our hardware partner. Cloud Matrix IT handles all warranty coordination, including:
• Return Merchandise Authorization (RMA) (submission of ticket required)
• Replacement logistics (client pays for return shipping)
• Replacement devices may differ from the original model depending on availability.
Coverage: This warranty provides coverage for any defects or malfunctions that may occur in the laptops and PCs you have purchased from Cloud Matrix IT and/or it’s third party distributors. The warranty covers the entire unit, ensuring that any issues with the device as a whole will be addressed and resolved under the terms of this warranty. If your laptop or PC experiences any defects or malfunctions within the warranty period, we will provide a complete advanced unit replacement to ensure your satisfaction and continued usage of our products
Duration: The warranty period is valid for a period of three (3) years from the date of purchase.
Advance Replacement: In the event of a covered component failure, we will provide you with an advance replacement unit at no additional cost. We will process a ground shipment of the replacement unit to you after approving your warranty claim.
Return of Faulty Component: Upon receiving a full unit advance replacement, you are required to return the faulty unit within 10 business days using the provided prepaid return ship label. Failure to return the faulty unit within the specified timeframe may result in additional charges. Some warranty claims may be resolved by sending an individual part (ex. laptop batteries) and will be at our discretion.
Warranty Transferability: This warranty is non-transferable and is only applicable to your business.
Warranty Exclusions: This warranty does not cover damage caused by misuse, accidents, acts of nature, unauthorized modifications, or any other circumstances beyond normal usage. Advanced replacement of damaged machines from these conditions may be available for a fee, determined per incident.
Support & Data Responsibility
Clients receive full support under the IT PROTECT platform, including:
• Remote hardware troubleshooting (if applicable)
• Device replacement coordination
• Data migration assistance (if applicable)
Important: Clients and end users are responsible for backing up data prior to any hardware failure or related issues. Cloud Matrix IT is not responsible for any data loss. We strongly recommend using SharePoint (for M365) or Google Drive (for Workspace) as designated backup solutions, or if the client is using their own backup solution.
Damage, Loss, and Limitations
• Clients are fully responsible for any device that is lost, stolen, or physically damaged during the 90 test drive window
• If a device is not returned, or is returned in poor condition during the 90 days test drive, the client will be invoiced for the agreed-upon purchase amount
• Devices must be managed under the IT PROTECT platform to remain eligible for support and warranty services
• Cloud Matrix IT does not offer trade-in, buyback, or recycling services. For policies related to device offboarding and end-of-life, please refer to the Endpoint Offboarding section below.
Help Desk Support Portal
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
As part of our IT PROTECT platform, every supported employee is provided with access to Cloud Matrix IT’s Dedicated Help Desk Support Portal—a centralized system for requesting assistance, tracking ticket progress, and communicating with our support team.
Easy Access & Ticket Submission
We offer multiple convenient ways for your team to get help when they need it:
• System Tray Icon (Recommended):
The easiest and most direct way to access the support portal is by clicking the IT PROTECT icon in the system tray on your desktop. From there, users can:
o Submit a new support request
o Check the status of existing tickets
o View updates and communication from our support team
• Email-Based Ticketing:
Users can also submit support requests by sending an email from their work email address to:
📧 support@cloudmatrixit.com
A ticket will be automatically generated, and users will receive updates via email as their issue is worked on.
• Web Portal Access:
Users can log into the client support portal through any web browser to view, manage, and comment on tickets.
Empowering Your Entire Team
Every supported employee in your organization is entitled to access the help desk. Whether the issue is a minor login problem or a critical outage, our team is standing by to help—quickly, professionally, and with full transparency.
By making IT support accessible and easy to use, we help keep your organization running smoothly while giving your team the confidence to request help the moment it’s needed.
IT Documentation
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT maintains comprehensive IT documentation for each managed client as part of our commitment to consistent service delivery, operational transparency, and long-term supportability. Our documentation framework is built on industry best practices and is trusted by thousands of IT service professionals across the globe.
What We Document
We take a systematic and structured approach to documenting your IT environment. This may include, but is not limited to:
• Network Diagrams & Infrastructure Maps
Visual representations of your network topology, including key components, configurations, and relationships (if we manage your network).
• Machine & Asset Inventory
Details on managed endpoints, servers, network equipment, and associated configurations or roles.
• On-Premises Configurations
Documentation of any physical infrastructure or systems located at your facility, including file servers, firewalls, switches, and backup appliances.
• Cloud Systems & SaaS Platforms
Configuration and access details for cloud services such as Microsoft 365, Google Workspace, Azure, and other third-party business-critical platforms.
• Credentials & Access Control
Securely documented (but not shared) access methods, administrative account tracking, MFA policies, and user permission structures.
• Operational Runbooks & SOPs
Internal procedures used by Cloud Matrix IT to manage your systems, respond to incidents, and execute maintenance tasks.
Access & Client Visibility
• Read-Only Access: At our discretion, clients may be granted limited, read-only access to portions of their IT documentation for auditing, compliance, or internal review purposes. While we manage this information the client will always own the data. We can export and send data to you when requested.
• Security & Confidentiality: All documentation is securely maintained and access-controlled. Sensitive information is protected using encryption and role-based access protocols.
By entrusting Cloud Matrix IT with your IT documentation, you gain the benefit of an organized, professional knowledge base built for consistency, continuity, and long-term success.
IT Help Desk Support
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides comprehensive Help Desk Support Services as part of our IT PROTECT platform, ensuring your employees receive fast, friendly, and effective technical assistance when they need it. Our help desk serves as the front line for resolving day-to-day IT issues, keeping your team productive and your systems running smoothly.
Scope of Support
Our Help Desk team assists with a wide range of common IT issues, including:
• Device troubleshooting (PCs, laptops, peripherals)
• Software installation and support
• Email access and configuration (Microsoft 365, Google Workspace)
• Password resets and login issues
• Printer and network connectivity problems
• Remote access and VPN issues
• Guidance on IT policies and security best practices
Support Availability
• Business Hours: Support is available Monday through Friday, 8:00 a.m. to 5:00 p.m. (Central Time), excluding federal holidays.
• After-Hours Support: Time-sensitive requests outside business hours may be addressed on a case-by-case basis depending on urgency and technician availability.
Ways to Request Support
We make it easy for your users to get help:
• IT PROTECT System Tray Icon: The most convenient way to request support—just click the icon in your desktop’s system tray to submit a ticket and access the support portal.
• Email: Send requests to support@cloudmatrixit.com using your work email to automatically generate a support ticket.
• Client Portal: Access your organization’s support portal to submit and track tickets, view updates, and communicate directly with our team.
Response & Resolution
• Ticket Triage: All incoming requests are triaged based on severity, business impact, and priority level.
• Service Level Expectations: We strive to respond to most tickets within 1–2 business hours and resolve standard issues as quickly as possible, depending on complexity and client availability.
Client Responsibilities
• Ensure staff are aware of proper ticket submission channels.
• Provide complete and accurate descriptions of issues when submitting support requests.
• Notify Cloud Matrix IT of any urgent issues that may disrupt business operations.
Please see Service Levels below for more information.
Microsoft 365 & Google Workspace License Management
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Note: While we do provide licensing through a third party and assist our clients with managing these licensing within their M365 tenant, we do not take ownership or “manage” our clients M365 tenants. We do, however, consult with our clients on the best practices and optimal security configurations to help protect them from cybersecurity incidents. We do not guarantee prevention. We help our clients procure licenses, create users, assign licenses to those users, and help those users with getting starting in using M365.
We offer license and user management services to our clients to help optimize their subscriptions, ensure compliance with best practice policies and regulations, and enhance the security and productivity of the environment. You can enjoy the following benefits:
• Save time and money by delegating the complex and tedious tasks of license allocation, usage monitoring, and billing to our experts.
• Reduce risks and liabilities by relying on our best practices and proven methodologies for license management and user administration.
• Increase user satisfaction and adoption by providing them with the right level of functionality and access.
• Leverage our experience and knowledge to get the most out of your investment and stay ahead of the curve.
High-level functions we provide as part of our service are:
License Requirement: When monitoring and managing M365 environments for our clients, it is required that we maintain at a minimum one(1) Microsoft Business Premium license within the tenant that is invoiced to the client as part of the service. Additionally, certain security requirements a Microsoft Entra ID 2 license may be required to provide additional security features.
License management: We help you select the best license plan for your organization, purchase and assign licenses to your users, track and report on license consumption and costs, and reclaim and reassign unused or inactive licenses. Licenses are purchased on a monthly subscription which affords you the flexibility in reclaiming licenses when they are no longer needed. Saving you on the costs of a yearly subscription.
User onboarding and offboarding: We help you create and manage user accounts, groups, and permissions in Microsoft Entra and Google Workspace, assign and revoke licenses, and configure user settings and preferences. We also help you securely offboard users when they leave your organization, by removing their access, licenses, and restrict data.
Multifactor authentication: We help you enable and enforce multifactor authentication (MFA) for your users, which adds an extra layer of security to their sign-in process. We also help you manage the MFA settings and methods for your users. We do not operate as an owner or make organizational changes outside general security settings without consulting with the client.
We are committed to providing you with the highest quality of service and support. However, we are not liable for any damages or losses that may arise from your use of our service, such as data breaches, service interruptions, or noncompliance issues. We also advise that you follow best practices and guidelines, and that you keep your users informed and educated about their responsibilities and obligations.
Microsoft 365 Managed Security with Active Monitoring, Assessment, & Alerting
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Powerful auditing, monitoring, and reporting on your Microsoft 365 environment to give you the complete picture of the security and configuration of your M365 tenant. This assessment & auditing solution will provide an in-depth and detailed review of your M365 environment. This assessment is completed within the onboarding period, and we will schedule a time with you to review post onboarding.
This critical solution provides insight into the 100s of security and configuration settings within M365, to include Azure, M365, Teams, SharePoint, and Security & Compliance Centers, to give you a complete picture of your M365 security posture. From this assessment we can work with you on a T&M basis to configure and secure your M365 environment. Periodically we review your M365 environment to make sure you're keeping with best practices.
Mobile Device Management (MDM)
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Mobile devices, such as smartphones, tablets, and laptops, are essential tools for today’s workforce. They enable your employees to work from anywhere, access your organization’s resources, and collaborate with their colleagues. However, managing and securing these devices can be challenging and time-consuming, especially if you have a large and diverse device fleet.
Services Provided
• Device/User onboarding and offboarding: Can assist with creating and managing user accounts, groups, and permissions, assigning and revoking device licenses, and configure device settings and preferences. We also help you securely offboard devices when they are lost, stolen, or no longer needed, by wiping or locking them remotely.
• Device patching: We help you keep your devices up to date with the latest security patches and software updates, ensuring that they are protected from vulnerabilities and bugs.
• Device security: We help you enforce device security policies, such as requiring a passcode, encryption, antivirus, and multifactor authentication. We also help you monitor and audit device activity, detect and respond to security incidents, and block or quarantine non-compliant devices.
• Identity management: We help you integrate your devices with your identity and access management system, such as Azure Active Directory, to enable single sign-on, conditional access, and role-based access control for your users and devices.
• Software Management: We work with you to manage and keep required software up to date on all managed mobile devices.
Terms, Conditions, & Requirements for MDM:
1. Apple Business Manager (ABM) is required in order to enroll and configure within our mobile device management system. This will require your business to have a DUNS (https://www.dnb.com/duns.html) number in place to set up ABM with Apple. Please see the following link for all requirements. https://support.apple.com/en-gu/guide/apple-business-manager/axm6d9dc7acf/web. We can assist you with requesting and setting up your ABM.
2. We require a user be created within your Apple Business Management environment as a Device Enrollment Manager in order to configure the mobile device management server token set up to configure MDB for your organization.
3. All devices will be required to be added to your ABM environment before they can be managed by our MDM
4. In order to fully manage devices properly, devices will need to be wiped and restored to factory before they can be enrolled in our MDM environment.
5. We will require a licensed account user with access to email within your domain (example: Microsoft 365 or Google Workspace) to facilitate the linkage and configuration of the MDM to your ABM.
6. All clients will be required to be set up within our secure PCI compliant payment portal to pay their monthly invoices. Please see payment terms within the Master Services Agreement located at: https://cloudmatrixit.com/cloud-matirix-it-msa.
All licenses are purchased on a 1 year agreement for the quantity initially ordered. Additional licenses may be purchased during the 1 year term if additional mobile devices are enrolled. Please note, all licenses will remain on the agreement until the agreement renews. The number of licenses may be reduced at the beginning of the next agreement.
Multifactor Authentication
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
We can assist you with the implementation and facilitation of a two factor authentication solution from a designated Third Party Provider. We do not own or manage the software on which you provide MFA to your organization. We show you how to configure and manage your MFA options throughout your environment.
• Advanced two factor authentication with advanced admin features.
• Secures on-premises and cloud-based applications.
• Permits custom access policies based on role, device, location.
• Identifies and verifies device health to detect “risky” devices
Network Management
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Offering a comprehensive service for managing your network infrastructure. We help you optimize your network performance, ensure reliability and availability, and enhance the security and compliance of your network.
Services Provided:
• Network Design and Infrastructure Setup: A cornerstone of managed network services, where the provider designs a robust and scalable network architecture. This includes setting up routers, switches, firewalls, and other necessary network hardware. The provider ensures the design meets the client's business needs, is secure from cyber threats, and has the capacity to grow.
• Security Management: A critical area that involves implementing security measures to protect the network against threats. This includes configuring firewalls (if applicable), setting up intrusion detection and prevention systems (if applicable), enforcing access controls, and regular security assessments to identify and mitigate vulnerabilities.
• Support and Troubleshooting: Providing ongoing support and rapid response to any network issues that arise. This includes a helpdesk for client inquiries, on-site or remote troubleshooting, and resolving hardware and software network failures to minimize downtime.
• Software Updates and Patch Management: Ensuring that all network-related software is up to date with the latest patches and updates to maintain security and performance. This includes managing updates for operating systems, firmware, and applications that are critical to network operations.
• Performance Optimization: Regular analysis and tweaking of the network to optimize performance. This involves adjusting network configurations, upgrading hardware, and employing quality of service (QoS) measures to ensure critical applications have the necessary resources.
• Backup and Disaster Recovery: Implementing and managing backup solutions to preserve data integrity and availability. This also includes developing and testing disaster recovery plans to ensure quick restoration of network functions in case of a catastrophic event.
• Compliance and Reporting: Ensuring that the network management practices adhere to relevant industry standards and regulations. Providing detailed reporting on network performance, incident management, and compliance status to the client for transparency and audit purposes.
• Vendor Management: Acting as a liaison between the client and third-party vendors for network-related services and equipment. This includes negotiating contracts, handling purchases and licenses, and managing service-level agreements (SLAs).
Requirements:
1. In order to provide network management, we will require full administrative access to all networking equipment in your environment.
2. We will also highly suggest that access to these devices is extremely limited with only a few administrative accounts.
In order to provide any or all the network management services, you may be required to update or replace some or all networking equipment to bring them up to industry standards. Any hardware replacement requirements will be billed separately and at the client’s expense.
Network Monitoring & Alerting
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Inventory
Gain complete visibility into your networks with real time automated device and attribute discovery. Asset Discovery which gives you 360-degree visibility and actionable insights on all network-based devices and IT infrastructures. Automated network mapping of your environment to allow you a visualization of your entire network.
Monitoring
Allows us to identify issues and troubleshoot in real time at network and device levels. Using SNMP resource monitoring will allow us to monitor all your important KPIs within your network. Can use WAN and LAN performance, statistics, measures, alerts and graphs to make sure your infrastructure is performing at its best.
Security
Automated networking scanning allows us to proactively scan for network vulnerabilities, looking for device changes, open ports, and can alert on custom parameters that are important to your organization.
Network monitoring & alerting is provided to help monitor, alert, and provide real time information to assist in troubleshooting network issues. Some devices may require credentials to provide certain data about the devices or networks. This service provides information only. Any remediation outside of these services are out of scope. Cloud Matrix IT can consult with you on remediation efforts and all costs are on a T&M basis.
Requirements:
1. Network monitoring, alerting, and assessments require our network agent to be installed on a machine within your network for a constant connection. If you maintain mobile devices that move in and out of your main network, it will be more difficult to provide continuous data to our agent.
2. It is highly suggested, but not required, that the machine the agent is installed on is wired to your network vs. wireless. Being wired to your network will give more accurate performance monitoring metrics to report and troubleshoot from.
3. Some devices on the network can be monitored in greater detail if our network agent has access to the device itself for reporting SNMP v3 data from the device. We will require the devices to have SNMP v3 turned on to provide that level of data if SNMP v3 is available to that device.
In order to provide any or all the monitoring services, you may be required to update or replace some or all networking equipment to bring them up to industry standards.
Password Management
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
Cloud Matrix IT provides password management services to clients through an enterprise-grade solution designed to enhance organizational security, simplify credential management, and support compliance efforts. As part of this service, we provision and support the deployment of a secure password management platform to you (Client) for your organization.
Service Scope
• Provisioning & Configuration: We assist with the setup, configuration, and onboarding process for your organization’s password management platform. This includes creating administrative accounts, setting organizational policies, and integrating with your existing IT environment where applicable.
• User Enablement: We will instruct your primary user how to enroll users into the platform and provide initial training and support to ensure effective adoption. We may assist in assigning roles or permissions in accordance with your organization's internal access policies.
• Technical Support: We provide support for password manager-related issues, including troubleshooting access problems, assisting with password policy enforcement, and coordinating with the software vendor for escalated issues if needed.
Data Access & Limitations
Please note the following critical limitations regarding our role in your password management:
• No Access to Vaults or Passwords: Cloud Matrix IT does not have access to client password vaults or the contents stored within them. All vault data is encrypted end-to-end and can only be accessed by the authorized users within your organization.
• Client-Managed Credentials: You are solely responsible for the creation, management, and security of individual passwords and stored credentials. Our team does not manage, store, or share your passwords.
• No Visibility into Password Sharing: We do not have the ability to view or control password sharing between users. All such sharing is governed by your internal administrative settings within the password management platform.
• Security Responsibility: While we provide the tools and support to enhance password security, the responsibility for maintaining secure and compliant usage lies with you, the client. This includes managing user permissions, enabling multi-factor authentication (MFA), and regularly reviewing access logs and audit trails.
Your Master Password: You hereby understand that upon using the Software, you will be required to create a "Master Password." The Master Password will be used by you and only you.
You are responsible for maintaining the security of your Master Password and records entered, imported and exported using the Software. Cloud Matrix IT has no knowledge of your Master Password and will not ask or be permitted to ask for your Master Password. Cloud Matrix IT, will not under any circumstances, have access to your Master Password or the records stored in Keeper.
You agree to not issue your Master Password to any third parties and shall not, under any circumstances, issue your Master Password to any customer support representative of Cloud Matrix IT in the event you contact Cloud Matrix IT for Software assistance. Generally, you will agree to not share your Master Password with any employee, agent, officer or director of Cloud Matrix IT. Cloud Matrix IT shall not be responsible for the actions of any individuals who misuse or misappropriate your Keeper information or other any of your assets using your Master Password or the information stored in the password manager.
Please remember your Master Password. If you lose or forget your Master Password, Cloud Matrix IT will not be able to assist you in gaining access to your records since Cloud Matrix IT does not have access to or knowledge of your Master Password. Again, it is imperative to not forget your Master Password since this is required to gain access to your records stored in the password manager.
While we may provide the consulting to manage company passwords securely, we are not, and will not be held liable for how you, the client, are managing those passwords and access to the service. This includes, but is not limited to, unauthorized access by any means, miss configuration of management of any data within this solution. The client is fully responsible for data entry and management of all data within the solution.
PCI Compliant Payment Portal
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
A PCI compliant payment portal will be provided to you and included with IT PROTECT to allow you to make easy and secure payments via credit card or ACH.
Privileged Access Management (PAM)
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
As part of Cloud Matrix IT’s ongoing efforts to continually improve security and the end user experience, we have further enhanced our IT PROTECT platform to help you more quickly process application updates that require administrator privileges. This solution will pre-authorize and fast-track the installation of approved applications (or software updates) while still protecting you from those that are malicious or unintended.
Our Privilege Access Management (PAM) solution that will save you time and make installing software updates seamless and very efficient. Saving you time from submitting a ticket and coordinating with us to process the install/update. Currently developed for Windows OS endpoints (MacOS being developed for a future release).
Remove Admin Privileges. Provide enhanced security to your servers & workstations by removing local Admin rights without frustrating end users.
Audit & Remediation. Audit machines with User Account Control (UAC) turned off across all of your clients and improve UAC security.
Malware protection. Elevation requests are automatically checked against Virus Total’s database giving real time insight into what the end user is requesting to install or update.
Security & Compliance. Meet Security & Compliance goals quickly. If you have insurance or compliance regulations that mandate a certain level of security, our PAM solution can quickly satisfy those needs.
Automated Rules. Make rules which automate future requests. Save time and improve your efficiency with automating privileged access management to automatically approve end user requests based on known software they regularly use.
Security Incident & Event Monitoring (SIEM)
Implementation and facilitation of this solution is from a designated Third Party Provider. We will not be held liable for any downtime or software related issues the third party may experience.
The SIEM service utilizes threat intelligence to detect threats that can exploit potential vulnerabilities against your managed network.
• Initial Assessment. Prior to implementing the SIEM service, we will perform an initial assessment of the managed network at your premises to define the scope of the devices/network to be monitored (the “Initial Assessment”).
• Monitoring. The SIEM service detects threats from external facing attacks as well as potential insider threats and attacks occurring inside the monitored network. Threats are correlated against known baselines to determine the severity of the attack.
• Alerts & Analysis. Threats are reviewed and analyzed by third-party human analysts to determine true/false positive dispositions and actionability. If it is determined that the threat was generated from an actual security-related or operationally deviating event (an “Event”), then you will be notified of that Event.
Events are triggered when conditions on the monitored system meet or exceed predefined criteria (the “Criteria”). Since the Criteria are established and optimized over time, the first thirty (30) days after deployment of the SIEM services will be used to identify a baseline of the Client’s environment and user behavior. During this initial thirty (30) day period, Client may experience some “false positives” or, alternatively, during this period not all anomalous activities may be detected.
Note: The SIEM service is a monitoring and alert-based system only; remediation of detected or actual threats are not within the scope of this service and may require Client to retain Cloud Matrix IT’s services on a time and materials basis.
Software Licensing
All software provided to you by or through Cloud Matrix IT is licensed, not sold, to you (“Software”). In addition to any Software-related requirements described in Cloud Matrix IT’s Master Services Agreement, Software may also be subject to end user license agreements (EULAs), acceptable use policies (AUPs), and other restrictions all of which must be strictly followed by you and any of your authorized users.
When installing/implementing software licenses in the managed environment or as part of the Services, we may accept (and you agree that we may accept) any required EULAs or AUPs on your behalf. You should assume that all Software has an applicable EULA and/or AUP to which your authorized users and you must adhere. If you have any questions or require a copy of the EULA or AUP, please contact us.
Strategic Planning
IT PROTECT includes Strategic Roadmap & IT Planning as a service to help you align your IT goals with your business objectives. It helps you plan and prioritize your IT projects, budget, and resources, and ensure that your IT infrastructure supports your current and future needs.
Your vCIO will help you analyze technical environments, establish IT standards, track feedback, and develop a customized strategic roadmap that maps to your business objectives.
Suggestions and advice rendered to you are provided in accordance with relevant industry practices, based on your specific needs and Cloud Matrix IT’s opinion and knowledge of the relevant facts and circumstances. By rendering advice, or by suggesting a particular service or solution, Cloud Matrix IT is not endorsing any particular manufacturer or service provider.
Strategic Roadmap & IT Planning is a huge value add to your business because it helps you: Optimize your IT investment and maximize your ROI, enhance your IT efficiency and productivity, and improve your IT security and compliance. Strategic Roadmap & IT Planning can include all or a combination of the following:
• A comprehensive assessment of your current IT environment, including your hardware, software, network, security, and performance.
• A detailed report that identifies your IT strengths, weaknesses, opportunities, and threats, and provides recommendations for improvement.
• A roadmap that outlines your IT vision, strategy, and action plan, and defines the scope, timeline, and cost of each IT project.
• A regular review and update of your roadmap and plan, to monitor your progress and adjust to changing needs and circumstances.
Reviews may be scheduled quarterly, or at the discretion of Cloud Matrix IT to review various topics such as the current state of IT management, roadmap items, or budgeting.
Virtual Chief Information Officer (vCIO)
Act as the main point of contact for certain business-related IT issues and concerns.
• Assist in creation of information/data-related plans and budgets.
• Provide strategic guidance and consultation across different technologies.
• Create company-specific best standards and practices.
• Provide education and recommendations for business technologies.
• Participate in scheduled meetings to maintain goals.
• Maintain technology documentation.
• Assess and make recommendations for improving technology usage and services.
Covered Environment
Managed Services will be applied to the number of devices indicated in the Quote (“Covered Hardware”). The list of Covered Hardware may be modified by mutual consent (email is sufficient for this purpose); however, we reserve the right to modify the list of Covered Hardware at any time if we discover devices that were not previously included in the list of Covered Hardware and which are receiving Services, or as necessary to accommodate changes to the quantity of Covered Hardware.
Unless otherwise stated in the Quote, Covered Devices will only include technology assets (such as computers, servers, and networking equipment) owned by the Client’s organization. As an accommodation, Cloud Matrix IT may provide guidance in connecting a personal device to the Client’s organization’s technology, but support of personal devices is generally not included in the Scope of Services.
If the Quote indicates that the Services are billed on a “per user” basis, then the Services will be provided for up to two (2) Business Devices used by the number of users indicated in the Quote. A “Business Device” is a device that (i) is owned or leased by Client and used primarily for business, (ii) is regularly connected to Client’s managed network, and (iii) has installed on it a software agent through which we (or our designated Third Party Providers) can monitor the device.
We will provide support for any software applications that are licensed through us. Such software (“Supported Software”) will be supported on a “best effort” basis only and any support required beyond Level 2-type support will be facilitated with the applicable software vendor/producer. Coverage for non-Supported Software is outside of the scope of the Quote and will be provided to you on a “best-effort” basis and a time and materials basis with no guarantee of remediation. Should our technicians provide you with advice concerning non-Supported Software, the provision of that advice should be viewed as an accommodation, not an obligation, to you.
If we are unable to remediate an issue with non-Supported Software, then you will be required to contact the manufacturer/distributor of the software for further support. Please note: Manufacturers/distributors of such software may charge fees, some of which may be significant, for technical support; therefore, we strongly recommend that you maintain service or support contracts for all non-Supported Software (“Service Contract”). If you request that we facilitate technical support for non-Supported Software and if you have a Service Contract in place, our facilitation services will be provided to you on a “best effort” basis.
In this Services Guide, Covered Hardware and Supported Software will be referred to as the “Environment” or “Covered Equipment.”
Cloud-Based Document Management on Local Devices
Cloud Matrix IT may assist the Client or end users with the installation and basic setup of cloud-based document management applications such as Microsoft OneDrive, SharePoint Sync, Google Drive for Desktop, Dropbox, Box, iCloud, and similar services (collectively, “Cloud Document Tools”). However, Cloud Matrix IT does not manage, monitor, or guarantee the functionality, performance, or synchronization status of these tools on any device.
The Client and its users are solely responsible for ensuring that Cloud Document Tools remain active and functional, and for verifying that files are being properly synchronized and stored in accordance with their internal data retention or backup policies. These applications can be disabled, paused, or misconfigured by the user, and Cloud Matrix IT does not provide continuous oversight or alerting in such cases.
Cloud Matrix IT shall not be liable for any data loss, failed synchronization, access issues, or application malfunctions related to Cloud Document Tools. Clients are expected to independently verify that their important data is being successfully stored in the intended cloud locations.
Device Availability Requirement
Client acknowledges and agrees that in order for Cloud Matrix IT to provide full management, monitoring, and support of covered devices under the IT PROTECT platform, such devices must remain powered on and connected to the internet. While certain endpoint protections may continue to function while offline, full service capabilities, including remote monitoring, patch management, security updates, data backup, and issue resolution, require active connectivity with modern internet connection speeds.
Cloud Matrix IT is not responsible for missed alerts, failed updates, delayed issue detection, or incomplete data backups on devices that are powered off, disconnected from the internet, or otherwise unavailable for remote access. It is the Client’s responsibility to ensure that managed devices remain accessible to Cloud Matrix IT systems to maintain the integrity and effectiveness of services delivered.
Physical Locations Covered by Services
Services will be provided remotely unless, in our discretion, we determine that an onsite visit is required. Cloud Matrix IT visits will be scheduled in accordance with the priority assigned to the issue (below) and are subject to technician availability. Unless we agree otherwise, all onsite Services will be provided at Client’s primary business location. Additional fees may apply for onsite visits: Please review the Service Level section below for more details.
Minimum Requirements / Exclusions
The scheduling, fees and provision of the Services are based upon the following assumptions and minimum requirements, all of which must be provided/maintained by the Client at all times:
• Server hardware must be under current warranty coverage.
• All equipment with Microsoft Windows® operating systems must be running then-currently supported versions of such software and have all the latest Microsoft service packs and critical updates installed.
• All software must be genuine, licensed, and vendor- or OEM-supported.
• Server file systems and email systems (if applicable) must be protected by licensed and up-to-date virus protection software.
• The managed environment must have a currently licensed, vendor-supported server-based backup solution that can be monitored.
• All wireless data traffic in the managed environment must be securely encrypted.
• All servers must be connected to working UPS devices.
• Recovery coverage assumes data integrity of the backups or the data stored on the backup devices. We do not guarantee the integrity of the backups or the data stored on the backup devices. Server restoration will be to the point of the last successful backup.
• Client must provide all software installation media and key codes in the event of a failure.
• Any costs required to bring the Environment up to these minimum standards are not included in the managed services agreement, unless listed in the quote, and are considered out of scope. All items required to bring the environment up to minimum standards will be quoted separately.
• Client must provide us with exclusive administrative privileges to the Environment.
• Client must not affix or install any accessory, addition, upgrade, equipment, or device on to the firewall, server, or NAS appliances (other than electronic data) unless expressly approved in writing by us.
Exclusions. Services that are not expressly described in the Quote will be out of scope and will not be provided to Client unless otherwise agreed, in writing, by Cloud Matrix IT. Without limiting the foregoing, the following services are expressly excluded, and if required to be performed, must be agreed upon by Cloud Matrix IT in writing:
Customization of third party applications, or programming of any kind.
Support for operating systems, applications, or hardware is no longer supported by the manufacturer.
Data/voice wiring or cabling services of any kind.
Battery backup replacement.
Equipment relocation.
The cost to bring the managed environment up to these minimum requirements (unless otherwise noted in the Quote).
The cost of repairs to hardware or any supported equipment or software, or the costs to acquire parts or equipment, or shipping charges of any kind.
Onboarding & Offboarding Devices
Endpoint Onboarding (Adding New Devices)
As part of our IT PROTECT platform, Cloud Matrix IT offers streamlined processes for onboarding and offboarding endpoint devices, ensuring all systems are properly configured, secured, and aligned with your business and compliance requirements. The client is responsible for all licenses associated with endpoints until they are fully offboarded.
Devices Purchased Through Cloud Matrix IT
Labor for setup, configuration, and onboarding is included at no additional charge when the endpoint is purchased directly through Cloud Matrix IT. Please see our Hardware Procurement section for more details.
Client-Provisioned Devices
Devices procured outside of Cloud Matrix IT will NOT incur additional fees as long as the client has coordinated with our Solutions Architects to purchase a compliant device. Otherwise there may be a fee assessed with onboarding the device.
Turnaround Time
Clients should coordinate with our Solution Architects when planning to onboard a new device or employees.
• We recommend planning new device or user onboardings at least 2–4 weeks in advance to ensure we can meet your requested timelines. Onboarding requests submitted outside of this planning window may result in delays and are not guaranteed.
• Please allow 1–2 business days for configuration after the initial agent is deployed. Timelines can vary depending on access to the device and/or scheduling with end user.
• Devices must be online and connected to the internet to complete onboarding. Offline devices cannot be fully configured.
• Cloud Matrix IT is not responsible for delays caused by missing hardware, incorrect device specifications, unlicensed software, or unavailable users during onboarding.
Urgent Onboarding Requests
Urgent onboarding requests (same-day or next business day) may be submitted through your vCIO.
A $249 Urgent Onboarding Request Fee will be applied to the next invoice if approved.
Service Scope – What’s Included
Onboarding includes the following standard services:
1. Deployment of the IT PROTECT platform and all required agents.
2. Installation of the baseline IT PROTECT configuration.
3. Creation of a standard account profile for the primary user.
4. Deployment of standard productivity tools (e.g., Microsoft 365 or Google Workspace), as determined in collaboration with the client.
5. Cloud Matrix IT administrative account will be installed on every managed device.
6. Onboarding checklist that has been developed with the client.
Any exceptions to the standard configuration must be reviewed and approved by Cloud Matrix IT and are handled on a case-by-case basis.
Device Compatibility & Standardization
Devices must meet minimum system requirements and be approved for IT PROTECT onboarding. Certain models, operating systems, or configurations may not be supported unless running on modern hardware. Clients are strongly encouraged to consult with Cloud Matrix IT Solution Architects prior to procuring hardware independently.
Operating System Upgrades
Any costs associated with OS upgrades are not included in onboarding services and will be quoted separately upon request.
Device Ownership & Licensing
• Clients are responsible for providing valid licensing for the operating system and all required software.
• Ownership of all hardware remains with the client (excluding any devices with unpaid invoices).
• Hardware costs are quoted separately and not included in onboarding labor.
Security & Compliance Requirements
Cloud Matrix IT must be informed of any compliance requirements (e.g., HIPAA, PCI) that apply to devices prior to onboarding. While the IT PROTECT platform supports general compliance frameworks, specific requirements must be communicated during the planning phase.
Endpoint Offboarding (Removing Devices)
Cloud Matrix IT ensures a secure and orderly transition when devices are removed from the IT PROTECT platform.
Client Responsibilities During Offboarding
• Notify Cloud Matrix IT of which device(s) are being offboarded (including hostname or user).
• Confirm whether the device is being repurposed, reassigned, or decommissioned entirely.
• Specify any data retention requirements or license changes.
• Ensure the device is online and accessible during the scheduled offboarding window.
Decommission Scheduling
Device offboarding requires 1–2 weeks lead time to schedule and execute. Clients are encouraged to plan decommissions in coordination with their vCIO or account manager.
Decommissioning Process
Labor to decommission a device is included for managed clients. The standard offboarding process includes:
• Removal of all IT PROTECT management tools and monitoring agents.
• Coordination with the client to ensure the device is no longer under Cloud Matrix IT management.
• Device will no longer be monitored, patched, or protected.
• No ongoing technical support will be provided for offboarded devices unless re-enrolled.
• Any issues that arise post-offboarding are the client’s responsibility.
Post-Offboarding Access
Upon decommissioning, Cloud Matrix IT will install a generic administrative user profile to provide the client with continued access to the device if needed.
Data Security & Retention
After a device is offboarded, it will no longer receive updates, security monitoring, or protection under the IT PROTECT platform.
• Clients are responsible for any data retention, encryption, or wiping procedures they wish to implement.
• Cloud Matrix IT does not provide data erasure or drive destruction services unless specifically requested and quoted.
• We will remove all user profiles from the machine during offboarding.
Licensing Retention
Software and cloud service licenses (e.g., Microsoft 365) remain under the client’s ownership.
If license deactivation or reallocation is required, clients must specify this in the offboarding request ticket.
Device End of Life
Devices that are either end of life or are no longer supported by the operating system’s manufacturer are considered out of compliance and will need to either offboarded/decommissioned or replaced by the client. The IT PROTECT solution will not operate on devices that are not compliant or supported by the OS manufacturer.
Onboarding & Offboarding Employees/Users
Cloud Matrix IT provides structured onboarding and offboarding support for employees and users as part of our IT PROTECT platform. These processes help ensure secure, consistent access to business-critical systems and effective deprovisioning to reduce organizational risk.
Ticket Submission & Authorization
All onboarding and offboarding requests must be submitted by the Client through the dedicated support portal. Only the business owner or a designated Point of Contact (POC) is authorized to submit such requests. Requests should include all pertinent information such as user’s name, start/end dates, required access, licensing instructions, and any special considerations.
We recommend a lead time of 1–2 weeks for new user onboarding to ensure full account and device readiness. Termination/offboarding requests must be submitted via ticket prior to the employee’s departure.
Note: Per our security policies, we configure our clients with standard user accounts vs administrative user accounts on their devices. This mitigates a very large risk when setting up user accounts/profiles on endpoints managed by IT PROTECT. Please see our Privilege Access Management (PAM) description above for more detailed information.
Onboarding Employees/Users
Onboarding includes two coordinated steps:
1. Account Configuration & Setup
• Execution of a customized onboarding checklist created in collaboration with the Client (Basic onboarding is included. If the client has a robust onboarding that requires extra time, there could be additional charges)
• Creation of user accounts in Microsoft 365, Google Workspace, or third-party applications (where access is provided)
• Assignment of appropriate licensing (if we manage M365 licensing)
• Configuration of system access and role-based permissions as defined by the Client
• Remote configuration of workstations and mobile devices (if enrolled in our MDM program)
• Implementation of security controls such as MFA setup (when supported) and assignment of temporary passwords
2. Technical Onboarding Meeting
Cloud Matrix IT technician will conduct a 30–45 minute onboarding session with the new user to:
• Review access to key systems and software
• Introduce the IT PROTECT platform and support tools
• Demonstrate how to submit tickets and request help
• Ensure connectivity and usability across all assigned devices and accounts
All onboarding processes are documented in our internal system and maintained in IT Glue.
Offboarding Employees/Users
When notified of employee separation, we follow a documented offboarding workflow that may include:
• Account suspension and/or removal from Microsoft 365, Google Workspace, and other managed services
• License removal and deallocation (if we manage the M365 tenant)
• Removal of the user from Cloud Matrix IT’s internal systems and monitoring
• Coordination with the Client to retain or transfer user data if needed
• Decommissioning of associated devices by removing the IT PROTECT platform and user profile (if the device is being retired)
For clients enrolled in our third-party SaaS management services, we will revoke access to those platforms based on the offboarding checklist previously developed with the Client.
Note: Cloud Matrix IT does not factory reset or wipe devices. The Client is responsible for maintaining administrative access to all hardware and ensuring its proper handling after user separation.
Exclusions & Limitations
• Cloud Matrix IT does not support personal accounts or personally owned hardware.
• MFA, password policy enforcement, and user permissions are configured based on Client input; enforcement and compliance are the Client’s responsibility unless otherwise contracted.
• Requests must be submitted through the Client’s ticketing portal.
Timeframe
While there is no formal SLA for employee onboarding or offboarding, these services are generally completed within the same business day or within 8 business hours from the time of ticket submission.
Personally Owned Equipment
Cloud Matrix IT permits the use of personally owned devices (“BYOD”) by employees of managed clients enrolled in the IT PROTECT platform, subject to the terms and limitations described below. While we support BYOD as a flexible option, we do so with strict boundaries regarding security, support, and liability.
Eligibility & Requirements
Personally owned laptops, desktops, tablets, and mobile phones may be enrolled in the IT PROTECT platform or our MDM solution, provided the following conditions are met:
• Devices must be actively supported by the manufacturer and capable of receiving software updates
• Devices must be enrolled in the IT PROTECT platform (or MDM) for any support to be provided
• Users must install and maintain Cloud Matrix IT’s designated security and management software
• Users and clients accept that the IT PROTECT platform may have full access to the device’s system-level data
Cloud Matrix IT does not support or allow BYOD systems that are outdated, unsupported, or incompatible with our platform standards.
Support Scope & Limitations
Support for BYOD systems is strictly limited to the functionality and health of the IT PROTECT platform and any management software deployed by Cloud Matrix IT. This may include:
• Installation and maintenance of endpoint protection and monitoring tools
• Basic hardware diagnostics and performance alerts (e.g., disk space, CPU usage)
• Assistance ensuring platform tools are running correctly
Cloud Matrix IT does not support:
• Device hardware failures or component repair
• Operating system troubleshooting not directly related to our tools
• Personal applications or data loss, regardless of cause
We do not warranty any personal device, and Cloud Matrix IT is not responsible for damages, data loss, or operational issues on BYOD hardware, or issues of any kind.
Security & Compliance
BYOD users must maintain the security tools provided by Cloud Matrix IT. This includes endpoint protection, remote monitoring agents, or MDM profiles, as applicable. While we will assist with installation and operation of these tools:
• We are not responsible if they are disabled, removed, or prevented from functioning due to user actions
• We do not enforce user role limitations (e.g., standard vs. admin accounts)
• We do not guarantee system integrity or protection from unauthorized access on BYOD devices
If a BYOD device poses a security risk or cannot support our tools, we may suspend support or recommend the device be removed from service.
Data Privacy & Access
By installing the IT PROTECT platform on a personal device, users acknowledge that:
• Cloud Matrix IT will have full system-level access to the device
• There is no implied privacy on the device
• We do not monitor or access private user data, but we do not separate business vs. personal content in our platform
All data on the device is potentially accessible to Cloud Matrix IT for the purposes of providing support, security monitoring, and compliance response. It is the user’s sole responsibility to safeguard personal content or use a separate device if privacy is a concern.
Client & User Responsibility
• The Client and end user are responsible for determining who is authorized to use a personal device for business purposes
• Clients must ensure that only approved, compatible personal devices are used within the business environment
• Cloud Matrix IT is not responsible for lost, stolen, or misused BYOD devices or data
Cloud Matrix IT will document all BYOD systems approved by the Client and enrolled in our platform.
Service Levels
Automated monitoring is provided on an ongoing (i.e., 24x7x365) basis. Response, repair, and/or remediation services (as applicable) will generally be provided during our business hours (currently M-F, 8 AM – 5 PM Eastern Time, excluding legal holidays and Cloud Matrix IT-observed holidays as listed below), unless otherwise specifically stated in the Quote or as otherwise described below.
We will respond to problems, errors, or interruptions in the provision of the Services during business hours in the timeframe(s) described below. Severity levels will be determined by Cloud Matrix IT in our discretion after consulting with the Client. All remediation services will initially be attempted remotely; Cloud Matrix IT may (in some cases) provide onsite service only if remote remediation is ineffective and, under all circumstances, only if covered under the Service plan selected by Client.
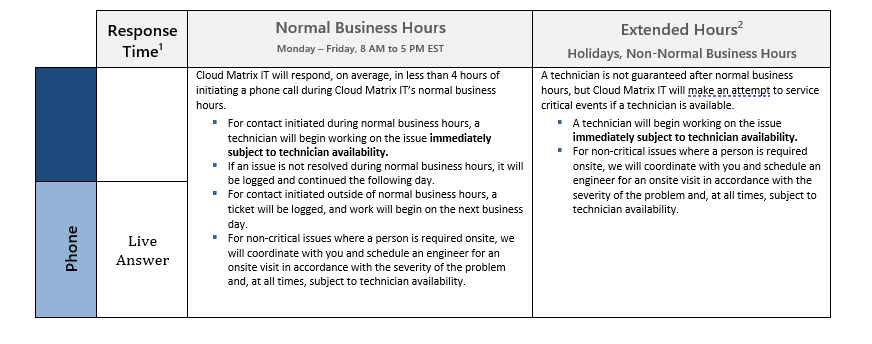
Response time is calculated from the time that the request for help is received by us though our designated support channels. Requests received in any other manner may result in delays or non-responses.
Extended Hours are not included and provided solely at the discretion of Cloud Matrix IT. If Extended Hours support is provided for critical issues/events, support hours will be billed to Client at our then-current the hourly rates with a one (1) hour minimum, 15 minute increments thereafter).

* All time frames are calculated as of the time that Cloud Matrix IT is notified of the applicable issue / problem by the Client through Cloud Matrix IT’s designated support portal, help desk support email, or by telephone at the telephone number listed in the Quote. Notifications received in any manner other than described herein may result in a delay in the provision of remediation efforts. Help desk support provided outside of our normal support hours will be billed to Client at our then-current the hourly rates with a one (1) hour minimum, 15 minute increments thereafter)
Onsite Support. Cloud Matrix IT primarily provides remote support to its managed clients; however, we can attempt to provide onsite services to our clients on a case by case basis and only at our discretion. As a premier cloud solutions provider, we make every effort to service our clients remotely before an onsite visit is scheduled. We offer onsite services on a time and materials basis at our then-current hourly rates with a three-hour minimum. Onsite support will be approved after the quote is signed and the initial minimum is paid by the client before scheduling a technician. Any additional hours spent onsite by the technician, or other Cloud Matrix IT professionals remotely, past the minimum will be invoiced when the onsite visit in completed.
Cloud Matrix IT-Observed Holidays: Cloud Matrix IT observes the following holidays:
• New Year’s Day
• Martin Luther King Jr. Day
• President’s Day
• Good Friday – Half Day
• Memorial Day
• Independence Day
• Labor Day
• Thanksgiving Day
• The day following Thanksgiving Day
• Christmas Eve
• Christmas Day
• New Year’s Eve – Half Day
Service Credits: Our service level target is 90% as measured over a calendar month (“Target Service Level”). If we fail to adhere to the Target Service Level and Client timely brings that failure to our attention in writing (as per the requirements of our Master Services Agreement), then Client will be entitled to receive a pro-rated service credit equal to 1/30 of that calendar month’s recurring service fees (excluding hard costs, licenses, etc.) for each day on which the Target Service Level is missed. Under no circumstances shall credits exceed 20% of the total monthly recurring service fees under an applicable Quote.
Fees
The fees for the Services will be as indicated in the Quote.
Reconciliation. Fees for certain Third Party Services that we facilitate or resell to you may begin to accrue prior to the “go-live” date of other applicable Services. (For example, Microsoft Azure or AWS-related fees begin to accrue on the first date on which we start creating and/or configuring certain hosted portions of the Environment; however, the Services that rely on Microsoft Azure or AWS may not be available to you until a future date). You understand and agree that you will be responsible for the payment of all fees for Third Party Services that are required to begin prior to the “go-live” date of Services, and we reserve the right to reconcile amounts owed for those fees by including those fees on your monthly invoices.
Changes to Environment. Initially, you will be charged the monthly fees indicated in the Quote. Thereafter, if the managed environment changes, or if the number of authorized users accessing the managed environment changes, then you agree that the fees will be automatically and immediately modified to accommodate those changes.
Travel Time. If onsite services are provided, we will travel up to 30 minutes from our office to your location at no charge. Time spent traveling beyond 30 minutes (e.g., locations that are beyond 30 minutes from our office, occasions on which traffic conditions extend our drive time beyond 30 minutes one-way, etc.) will be billed to you at our then current hourly rates unless otherwise stated in the quote. In addition, you will be billed for all tolls, parking fees, and related expenses that we incur if we provide onsite services to you.
Appointment Cancellations. You may cancel or reschedule any appointment with us at no charge by providing us with notice of cancellation at least one business day in advance. If we do not receive timely a notice of cancellation/re-scheduling, or if you are not present at the scheduled time or if we are otherwise denied access to your premises at a pre-scheduled appointment time, then you agree to pay us a cancellation fee equal to two (2) hours of our normal consulting time (or non-business hours consulting time, whichever is appropriate), calculated at our then-current hourly rates.
Access Licensing. One or more of the Services may require us to purchase certain “per seat” or “per device” licenses (often called “Access Licenses”) from one or more Third Party Providers. (Microsoft “New Commerce Experience” licenses as well as Cisco Meraki “per device” licenses are examples of Access Licenses.) Access Licenses cannot be canceled once they are purchased and often cannot be transferred to any other customer. For that reason, you understand and agree that regardless of the reason for termination of the Services, fees for Access Licenses are non-mitigatable and you are required to pay for all applicable Access Licenses in full for the entire term of those licenses. Provided that you have paid for the Access Licenses in full, you will be permitted to use those licenses until they expire.
Discounted Project Rates. As an IT PROTECT managed client, you will have access to discounted project rates. The rate will depend on the type of project that is being developed and the level of expertise needed during the project. The discounted rate is 20% off our regular billable hourly rate. This discount will apply to hourly work we perform for you and will not apply to any third party tools and their rates.
After Hours Help Desk Support. Help desk support (remote support) provided outside of our normal support hours (M-F 8 a.m. to 5 p.m.) will be billed to the Client at our then-current hourly rates with a one (1) hour minimum, billed in 15 min increments thereafter.
Term; Termination
The Services will commence, and billing will begin, on the date indicated in the Quote (“Commencement Date”) and will continue through the initial term listed in the Quote (“Initial Term”). We reserve the right to delay the Commencement Date until all onboarding/transition services (if any) are completed, and all deficiencies / revisions identified in the onboarding process (if any) are addressed or remediated to Cloud Matrix IT’s satisfaction.
The Services will continue through the Initial Term until terminated as provided in the Agreement, the Quote, or as indicated in this Service Guide (the “Service Term”).
Per Seat/Per Device Licensing: Regardless of the reason for the termination of the Services, you will be required to pay for all per seat or per device licenses that we acquire on your behalf. Please see “Access Licensing” in the Fees section above for more details.
Removal of Software Agents; Return of Firewall & Backup Appliances: Unless we expressly direct you to do so, you will not remove or disable, or attempt to remove or disable, any software agents that we installed in the managed environment or any of the devices on which we installed software agents. Doing so without our guidance may make it difficult or impracticable to remove the software agents, which could result in network vulnerabilities and/or the continuation of license fees for the software agents for which you will be responsible, and/or the requirement that we remediate the situation at our then-current hourly rates, for which you will also be responsible. Depending on the particular software agent and the costs of removal, we may elect to keep the software agent in the managed environment but in a dormant and/or unused state.
Within ten (10) days after being directed to do so, you must remove, package and ship, at your expense and in a commercially reasonable manner, all hardware, equipment, and accessories leased, loaned, rented, or otherwise provided to you by Cloud Matrix IT “as a service.” If you fail to timely return all such equipment to us, or if the equipment is returned to us damaged (normal wear and tear excepted), then we will have the right to charge you, and you hereby agree to pay, the replacement value of all such unreturned or damaged equipment.
Client Offboarding
In the event that a client chooses not to renew their agreement with Cloud Matrix IT, or is released from service at our discretion, Cloud Matrix IT will initiate a formal offboarding process to responsibly conclude services, protect client data, and ensure a smooth transition.
Subject to the requirements in the MSA, Cloud Matrix IT will off-board Client from Cloud Matrix IT’s services by performing one or more of the following:
• Removal / disabling of monitoring agents in the Environment.
• Removal / disabling of endpoint software from the Environment.
• Removal / disabling of Microsoft 365 from the Environment (unless the licenses for Microsoft 365 are being transferred to your incoming provider; please speak to your technician for details.)
• Termination of SQL or Remote Desktop licenses provided by Cloud Matrix IT.
• Removal of credentials from the Environment.
• Removal of backup software from the Environment.
Decommissioning & Software Removal
At the conclusion of the agreement, Cloud Matrix IT will:
• Remotely uninstall the IT PROTECT platform and related management software from all applicable devices
• Decommission any SaaS solutions we previously managed or administered
• Coordinate with the client as needed for systems that cannot be fully decommissioned remotely
Devices will retain a local administrative account, allowing the client to maintain access and manage the hardware independently. Devices will not be wiped or factory reset.
Licensing & Access
For clients using Microsoft 365 or Google Workspace:
• Cloud Matrix IT will ensure that the client has at least one Global Administrator user prior to termination
• If Cloud Matrix IT provides licensing, clients will receive notice, typically 30 days or more, to secure replacement licensing
• All Cloud Matrix IT-managed licenses will be removed upon service termination and the client will be responsible for retaining their own licenses
Access to Cloud Matrix IT services, including the client portal, documentation systems, and support platforms, will be fully disabled as of the final decommission date.
Documentation & Data
Cloud Matrix IT will provide the client with all documentation and credentials maintained in our systems (such as IT Glue) prior to the termination date. This includes network information, licensing data, device inventories, and other technical records.
All backups and data stored or managed through the IT PROTECT platform will be permanently deleted at the time of service termination. Clients are solely responsible for implementing a new backup strategy beyond that date. Cloud Matrix IT does not retain any client data post-offboarding.
Final Billing & Contract Obligations
Clients are responsible for all fees and service charges incurred through the official decommission date. No refunds or proration will be provided. In cases of early termination by the client, the client remains responsible for payment of the full contract balance as outlined in the Master Services Agreement.
Transitioning to Another IT Provider
If the client transitions to a new IT provider, Cloud Matrix IT will make reasonable efforts to collaborate with the incoming provider to facilitate a smooth and timely handover of services. This may include providing documentation, confirming system statuses, and answering general technical questions related to the client's environment.
Cloud Matrix IT will not install, support, or manage any third-party platforms, agents, or solutions introduced by the incoming provider. Our support during this transition is strictly limited to reasonable coordination and the decommissioning of our own systems and tools.
Promotions & Discounts
From time to time, Cloud Matrix IT may, at its sole discretion, offer promotional pricing incentives to new clients who sign up for the IT PROTECT platform. These promotions are intended to provide added value during onboarding and may take the form of reduced monthly service fees or waived onboarding costs.
Eligibility & Scope
Promotions are:
• Available only to new clients who enroll in the IT PROTECT platform
• Applied exclusively to monthly recurring services under the IT PROTECT agreement
• Issued on a case-by-case basis and subject to approval by Cloud Matrix IT
• Non-transferable and not available to existing clients, unless explicitly approved in writing
Discounts do not apply to any additional services, line items, or project-based work billed separately from IT PROTECT.
Free Month Equivalents
Cloud Matrix IT may provide a promotional “free month” of service by applying a prorated discount across multiple months. For example, a client may receive:
• Two months at 50% off
• Or other partial discounts over time that total the equivalent value of one month free
The structure, timing, and application of promotional credits are determined solely by Cloud Matrix IT and may vary. Clients are not permitted to request or dictate how the promotion is applied.
Term Requirements & Early Termination
Promotions are only available to clients who agree to a minimum 12-month contract term. If the client terminates the contract early for any reason, per the MSA:
• The client will be responsible for the full value of the contract through the end of the term
• Any previously applied promotional credits or discounts will be added to the final invoice
Limitations & Disclaimers
• Promotions cannot be combined with other discounts, offers, or incentives unless explicitly approved in writing by Cloud Matrix IT
• All promotional terms will be included in the official quote provided to the client
• Cloud Matrix IT reserves the right to revoke, modify, or cancel any promotion at any time, for any reason
Referral Program
Cloud Matrix IT offers a Referral Program as a way to reward existing clients who introduce new businesses to our IT PROTECT platform. This program helps foster a trusted network of clients while providing meaningful value for referrals that lead to new partnerships.
Who Can Refer
The Referral Program is available to existing clients of Cloud Matrix IT. Both the client organization and the individual employee who made the referral may be eligible to receive rewards, provided the referred business signs a qualifying agreement. Clients may refer multiple businesses, and for each successful referral, both the referring client and individual may earn rewards.
Rewards
When a referred business signs a 12-month IT PROTECT agreement, the following rewards may apply:
• A discount of 15%–20% off one future monthly invoice for both the referring client and the new client
• A cash bonus to the individual who made the referral (typically less than $500 USD)
The amount, timing, and structure of all rewards are determined at the sole discretion of Cloud Matrix IT. Discounts may be applied to an invoice of our choosing, and cash rewards are typically issued within 30 to 90 days of the new client's contract start date.
Eligibility Requirements
To qualify:
• The referred business must not already be engaged with Cloud Matrix IT (e.g., previously met or quoted)
• The referred business must sign a minimum 12-month agreement for IT PROTECT
• The referral must be disclosed prior to the new client signing their agreement
Failure to disclose the referral before agreement execution will disqualify the referring party from receiving rewards.
Program Terms
• There is no cap on the number of referrals a client or individual can make
• Referring clients retain their reward even if the new client cancels early
• However, if the referred client cancels early, they will be responsible for reimbursing any rewards issued to them
• Promotions, discounts, and referral incentives may not be combined unless explicitly approved by Cloud Matrix IT
• All rewards must be confirmed in writing or on the signed quote
Cloud Matrix IT reserves the right to modify, withhold, or cancel any referral reward at its discretion. Program terms may change at any time.
Partner Program
As part of our commitment to helping businesses grow and succeed, Cloud Matrix IT offers a Partner Program exclusively for clients enrolled in our IT PROTECT platform. This program provides access to a trusted network of professional service providers across a variety of specialties.
Access to Trusted Professionals
Over the years, we’ve built relationships with a select group of partners in areas such as:
• Business consulting
• Marketing and branding
• Accounting and bookkeeping
• Legal services
• Telecommunications and low-voltage cabling
• Specialized technology & professional service vendors
Each partner in our network has either worked with Cloud Matrix IT directly or comes recommended through trusted relationships. When a client expresses a goal, challenge, or service need that falls outside our core capabilities, we may suggest and facilitate an introduction to a partner who can help.
How It Works
• Partner referrals are available exclusively to active IT PROTECT clients
• Cloud Matrix IT will first consult with the client to understand the specific objective or problem
• If appropriate, we’ll make a direct introduction to a qualified partner
• From there, the partner and client will communicate and work independently of Cloud Matrix IT
While we may receive a referral fee in some instances, most introductions are made strictly for the benefit of our clients and carry no ongoing involvement or compensation.
Program Boundaries
Please note:
• Cloud Matrix IT does not participate in, manage, or oversee any projects or agreements between the client and the referred partner
• We are not responsible for the work, recommendations, or performance of any third-party provider
• All financial, legal, or operational arrangements are made directly between the client and the partner
Additional Policies
The following additional policies (“Policies”) apply to Services that we provide or facilitate under a Quote. By accepting a Service for which one or more of the Policies apply, you agree to the applicable Policy.
Authenticity
Everything in the managed environment must be genuine and licensed, including all hardware, software, etc. If we ask for proof of authenticity and/or licensing, you must provide us with such proof. All minimum hardware or software requirements as indicated in a Quote or this Services Guide (“Minimum Requirements”) must be implemented and maintained as an ongoing requirement of us providing the Services to you.
Monitoring Services; Alert Services
Unless otherwise indicated in the Quote, all monitoring and alert-type services are limited to detection and notification functionalities only. Monitoring levels will be set by Cloud Matrix IT, and Client shall not modify these levels without our prior written consent.
Configuration of Third Party Services
Certain third party services provided to you under a Quote may provide you with administrative access through which you could modify the configurations, features, and/or functions (“Configurations”) of those services. However, any modifications of Configurations made by you without authorization could disrupt the Services and/or cause a significant increase in the fees charged for those third party services. For that reason, we strongly advise you to refrain from changing the Configurations unless we authorize those changes. You will be responsible for paying any increased fees or costs arising from or related to changes to the Configurations.
Modification of Environment
Changes made to the Environment without our prior authorization or knowledge may have a substantial, negative impact on the provision and effectiveness of the Services and may impact the fees charged under the Quote. You agree to refrain from moving, modifying, or otherwise altering any portion of the Environment without our prior knowledge or consent. For example, you agree to refrain from adding or removing hardware from the Environment, installing applications on the Environment, or modifying the configuration or log files of the Environment without our prior knowledge or consent.
Anti-Virus; Anti-Malware; EDR
Our anti-virus / anti-malware solution will assist in protecting the Environment from becoming infected with new viruses and malware (“Malware”); however, Malware that exists in the Environment at the time that the security solution is implemented may not be capable of being removed without additional services, for which a charge may be incurred. We do not warrant or guarantee that all Malware will be detected, avoided, or removed, or that any data erased, corrupted, or encrypted by Malware will be recoverable. To improve security awareness, you agree that Cloud Matrix IT or its designated third party affiliate may transfer information about the results of processed files, information used for URL reputation determination, security risk tracking, and statistics for protection against spam and malware. Any information obtained in this manner does not and will not contain any personal or confidential information.
Breach/Cyber Security Incident Recovery
Unless otherwise expressly stated in the Quote, the scope of the Managed Services Agreement does not include the remediation and/or recovery from a Security Incident (defined below). Such services, if requested by you, will be provided on a time and materials basis under our then-current hourly labor rates. Given the varied number of possible Security Incidents, we cannot and do not warrant or guarantee (i) the amount of time required to remediate the effects of a Security Incident (or that recovery will be possible under all circumstances), or (ii) that all data or systems impacted by the incident will be recoverable or remediated. For the purposes of this paragraph, a Security Incident means any unauthorized or impermissible access to or use of the Environment, or any unauthorized or impermissible disclosure of Client’s confidential information (such as user names, passwords, etc.), that (i) compromises the security or privacy of the information or applications in, or the structure or integrity of, the managed environment, or (ii) prevents normal access to the managed environment, or impedes or disrupts the normal functions of the managed environment.
Cloud Matrix IT is a managed service provider (MSP) and not a dedicated managed security services provider (MSSP), incident response (IR) firm, or forensic investigation company. As such, our capabilities in responding to large-scale cyberattacks, ransomware, or business-wide compromises are inherently limited. We do not provide legal, forensic, or regulatory services of any kind. In the event of a suspected or confirmed Security Incident, Cloud Matrix IT will notify the Client’s designated leadership and may assist with basic containment or response actions such as isolating affected systems, resetting credentials, or reviewing local logs. Where appropriate, we may provide technical context, recent monitoring data, or historical configuration records to aid in understanding the scope or origin of the incident.
For smaller, manageable incidents, Cloud Matrix IT may assist with remediation and recovery within the limits of our platform and available tools. However, in the event of a major or widespread compromise, Cloud Matrix IT will not lead the recovery process. Instead, we will advise the Client to engage a qualified incident response provider or utilize resources made available through their cyber insurance carrier. In such cases, we will coordinate with authorized third-party cybersecurity response team as needed and will provide relevant logs or supporting information when requested.
Clients are solely responsible for maintaining an internal incident response plan and for complying with all legal or regulatory reporting obligations resulting from a Security Incident. While not required, we strongly recommend that Clients maintain active cyber insurance coverage to support the costs associated with forensics, breach notification, legal consultation, and post-incident remediation. Cloud Matrix IT can provide general assistance in developing incident response plans as a separately billed project, but we do not assume responsibility for the enforcement or execution of such plans.
Recovery support, where requested, is limited to systems and data that are covered under our managed services platform. If Cloud Matrix IT provides the Client’s backup solution, we will attempt data restoration using the most recent successful backup, provided the system is operational and properly licensed at the time of the event. The integrity and availability of those backups, however, are not guaranteed. Restoration support for systems not under our management, or backups maintained by other vendors, is outside the scope of the agreement and are not supported.
Our ability to assist with response or recovery depends on the Client’s timely cooperation, including access to affected devices, participation in remediation steps, and adherence to our security recommendations. Any delays or limitations resulting from unavailable endpoints, revoked access, or uncoordinated third-party changes may restrict our ability to provide meaningful support. Additionally, if recovery actions are required outside of normal business hours or fall outside the scope of the Client’s service agreement, the associated time will be invoiced separately on a time & material basis.
For the purposes of this section, a “Security Incident” is defined as any unauthorized or impermissible access to or use of the managed environment, or any unauthorized disclosure of Client data—including usernames, passwords, or other sensitive information—that compromises the confidentiality, integrity, or availability of the environment, prevents normal system access, disrupts critical functions, or involves the introduction of ransomware, malware, or unauthorized administrative controls.
Environmental Factors
Exposure to environmental factors, such as water, heat, cold, or varying lighting conditions, may cause installed equipment to malfunction. Unless expressly stated in the Quote, we do not warrant or guarantee that installed equipment will operate error-free or in an uninterrupted manner, or that any video or audio equipment will clearly capture and/or record the details of events occurring at or near such equipment under all circumstances.
Fair Usage Policy
Our Fair Usage Policy (“FUP”) applies to all services that are described or designated as “unlimited” or which are not expressly capped in the number of available usage hours per month. An “unlimited” service designation means that, subject to the terms of this FUP, you may use the applicable service as reasonably necessary for you to enjoy the use and benefit of the service without incurring additional time-based or usage-based costs. However, unless expressly stated otherwise in the Quote, all unlimited services are provided during our normal business hours only and are subject to our technicians’ availability, which cannot always be guaranteed. In addition, we reserve the right to assign our technicians as we deem necessary to handle issues that are more urgent, critical, or pressing than the request(s) or issue(s) reported by you. Consistent with this FUP, you agree to refrain from (i) creating urgent support tickets for non-urgent or non-critical issues, (ii) requesting excessive support services that are inconsistent with normal usage patterns in the industry (e.g., requesting support in lieu of training), (iii) requesting support or services that are intended to interfere, or may likely interfere, with our ability to provide our services to our other customers.
Hosted Email
You are solely responsible for the proper use of any hosted email service provided to you (“Hosted Email”).
Hosted Email solutions are subject to acceptable use policies (“AUPs”), and your use of Hosted Email must comply with those AUPs—including ours. In all cases, you agree to refrain from uploading, posting, transmitting or distributing (or permitting any of your authorized users of the Hosted Email to upload, post, transmit or distribute) any prohibited content, which is generally content that (i) is obscene, illegal, or intended to advocate or induce the violation of any law, rule or regulation, or (ii) violates the intellectual property rights or privacy rights of any third party, or (iii) mischaracterizes you, and/or is intended to create a false identity or to otherwise attempt to mislead any person as to the identity or origin of any communication, or (iv) interferes or disrupts the services provided by Cloud Matrix IT or the services of any third party, or (v) contains Viruses, trojan horses or any other malicious code or programs. In addition, you must not use the Hosted Email for the purpose of sending unsolicited commercial electronic messages (“SPAM”) in violation of any federal or state law. Cloud Matrix IT reserves the right, but not the obligation, to suspend Client’s access to the Hosted Email and/or all transactions occurring under Client’s Hosted Email account(s) if Cloud Matrix IT believes, in its discretion, that Client’s email account(s) is/are being used in an improper or illegal manner.
Backup (BDR) Services
All data transmitted over the Internet may be subject to malware and computer contaminants such as viruses, worms and trojan horses, as well as attempts by unauthorized users, such as hackers, to access or damage Client’s data. Neither Cloud Matrix IT nor its designated affiliates will be responsible for the outcome or results of such activities.
BDR services require a reliable, always-connected internet solution. Data backup and recovery time will depend on the speed and reliability of your internet connection. Internet and telecommunications outages will prevent the BDR services from operating correctly. In addition, all computer hardware is prone to failure due to equipment malfunction, telecommunication-related issues, etc., for which we will be held harmless. Due to technology limitations, all computer hardware, including communications equipment, network servers and related equipment, has an error transaction rate that can be minimized, but not eliminated. Cloud Matrix IT cannot and does not warrant that data corruption or loss will be avoided, and Client agrees that Cloud Matrix IT shall be held harmless if such data corruption or loss occurs. Client is strongly advised to keep a local backup of all of stored data to mitigate against the unintentional loss of data.
Procurement
Equipment and software procured by Cloud Matrix IT on Client’s behalf (“Procured Equipment”) may be covered by one or more manufacturer or provider warranties, which will be passed through to Client to the greatest extent possible. By procuring equipment or software for the Client, Cloud Matrix IT does not make any warranties or representations regarding the quality, integrity, or usefulness of the Procured Equipment. Certain equipment or software, once purchased, may not be returnable or, in certain cases, may be subject to third party return policies and/or re-stocking fees, all of which shall be Client’s responsibility in the event that a return of the Procured Equipment is requested. Cloud Matrix IT is not a warranty service or repair center. Cloud Matrix IT will facilitate the return or warranty repair of Procured Equipment; however, Client understands and agrees that (i) the return or warranty of Procured Equipment is governed by the terms of the warranties (if any) governing the applicable Procured Equipment, for which Cloud Matrix IT will be held harmless, and (ii) Cloud Matrix IT is not responsible for the quantity, condition, or timely delivery of the Procured Equipment once the equipment has been tendered to the designated shipping or delivery courier.
Business Review / IT Strategic Planning Meetings
We strongly suggest that you participate in business review/strategic planning meetings as may be requested by us from time to time. These meetings are intended to educate you about recommended (and potentially crucial) modifications to your IT environment, as well as to discuss your company’s present and future IT-related needs. These reviews can provide you with important insights and strategies to make your managed IT environment more efficient and secure. You understand that by suggesting a particular service or solution, we are not endorsing any specific manufacturer or service provider.
vCIO Services
The advice and suggestions provided by us in our capacity as a virtual chief technology or information officer (if applicable) will be for your informational and/or educational purposes only. Cloud Matrix IT will not hold an actual director or officer position in Client’s company, and we will neither hold nor maintain any fiduciary relationship with Client. Under no circumstances shall Client list or place Cloud Matrix IT on Client’s corporate records or accounts.
Sample Policies, Procedures.
From time to time, we may provide you with sample (i.e., template) policies and procedures for use in connection with Client’s business (“Sample Policies”). The Sample Policies are for your informational use only, and do not constitute or comprise legal or professional advice, and the policies are not intended to be a substitute for the advice of competent counsel. You should seek the advice of competent legal counsel prior to using or distributing the Sample Policies, in part or in whole, in any transaction. We do not warrant or guarantee that the Sample Policies are complete, accurate, or suitable for your (or your customers’) specific needs, or that you will reduce or avoid liability by utilizing the Sample Policies in your (or your customers’) business operations.
Penetration Testing: Vulnerability Scanning
You understand and agree that security devices, alarms, or other security measures, both physical and virtual, may be tripped or activated during the penetration testing and/or vulnerability scanning processes, despite our efforts to avoid such occurrences. You will be solely responsible for notifying any monitoring company and all law enforcement authorities of the potential for “false alarms” due to the provision of the penetration testing or vulnerability scanning services, and you agree to take all steps necessary to ensure that false alarms are not reported or treated as “real alarms” or credible threats against any person, place, or property. Some alarms and advanced security measures, when activated, may cause the partial or complete shutdown of the Environment, causing substantial downtime and/or delay to your business activities. We will not be responsible for any claims, costs, fees, or expenses arising or resulting from (i) any response to the penetration testing or vulnerability scanning services by any monitoring company or law enforcement authorities, or (ii) the partial or complete shutdown of the Environment by any alarm or security monitoring device.
No Third Party Scanning
Unless we authorize such activity in writing, you will not conduct any test, nor request or allow any third party to conduct any test (diagnostic or otherwise), of the security system, protocols, processes, or solutions that we implement in the managed environment (“Testing Activity”). Any services required to diagnose or remediate errors, issues, or problems arising from unauthorized Testing Activity are not covered under the Quote, and if you request us (and we elect) to perform those services, those services will be billed to you at our then-current hourly rates.
Obsolescence
If at any time any portion of the managed environment becomes outdated, obsolete, reaches the end of its useful life, or acquires “end of support” status from the applicable device’s or software’s manufacturer (“Obsolete Element”), then we may designate the device or software as “unsupported” or “non-standard” and require you to update the Obsolete Element within a reasonable time period. If you do not replace the Obsolete Element reasonably promptly, then in our discretion we may (i) continue to provide the Services to the Obsolete Element using our “best efforts” only with no warranty or requirement of remediation whatsoever regarding the operability or functionality of the Obsolete Element, or (ii) eliminate the Obsolete Element from the scope of the Services by providing written notice to you (email is sufficient for this purpose). In any event, we make no representation or warranty whatsoever regarding any Obsolete Element or the deployment, service level guarantees, or remediation activities for any Obsolete Element.
Licenses
If we are required to re-install or replicate any software provided by you as part of the Services, then it is your responsibility to verify that all such software is properly licensed. We reserve the right, but not the obligation, to require proof of licensing before installing, re-installing, or replicating software into the managed environment. The cost of acquiring licenses is not included in the scope of the Quote unless otherwise expressly stated therein.
VOIP – Dialing 911 (Emergency) Services
The following terms and conditions apply to your use of any VoIP service that we facilitate for you or that is provided to you by a third party provider of such service. Please note, by using VoIP services you agree to the provisions of the waiver at the end of this section. If you do not understand or do not agree with any of the terms below, you must not subscribe to, use, or rely upon any VoIP service and, instead, you must contact us immediately. There is an important difference in how 9-1-1 (i.e., emergency) services can be dialed using a VoIP service as compared to a traditional telephone line. Calling emergency services using a VoIP service is referred to as “E911.”
Registration
You are responsible for activating the E911 dialing feature by registering the address where you will use the VoIP service. This will not be done for you, and you must take this step on your own initiative. To do this, you must log into your VoIP control panel and provide a valid physical address. If you do not take this step, then E911 services may not work correctly, or at all, using the VoIP service. Emergency service dispatchers will only send emergency personnel to a properly registered E911 service address.
Location
The address you provide in the control panel is the location to which emergency services (such as the fire department, the police department, etc.) will respond. For this reason, it is important that you correctly enter the location at which you are using the VoIP services. PO boxes are not proper addresses for registration and must not be used as your registered address. Please note, even if your account is properly registered with a correct physical address, (i) there may be a problem automatically transmitting a caller's physical location to the emergency responders, even if the caller can reach the 911 call center, and (ii) a VoIP 911 call may go to an unstaffed call center administrative line or be routed to a call center in the wrong location. These issues are inherent to all VoIP systems and services. We will not be responsible for, and you agree to hold us harmless from, any issues, problems, incidents, damages (both bodily- and property-related), costs, expenses, and fees arising from or related to your failure to register timely and correctly your physical location information into the control panel.
Address Change(s)
If you change the address used for E911 calling, the E911 services may not be available and/or may operate differently than expected. Moreover, if you do not properly and promptly register a change of address, then emergency services may be directed to the location where your services are registered and not where the emergency may be occurring. For that reason, you must register a change of address with us through the VoIP control panel no less than three (3) business days prior to your anticipated move/address change. Address changes that are provided to us with less than three (3) business days notice may cause incorrect/outdated information to be conveyed to emergency service personnel. If you are unable to provide us with at least three (3) business days notice of an address change, then you should not rely on the E911 service to provide correct physical location information to emergency service personnel. Under those circumstances, you must provide your correct physical location to emergency service dispatchers if you call them using the VoIP services.
If you do not register the VoIP service at your location and you dial 9-1-1, that call will be categorized as a “rogue 911 call.” If you are responsible for dialing a rogue 911 call, you will be charged a non-refundable and non-disputable fee of $250/call.
Power Loss
If you lose power or there is a disruption to power at the location where the VoIP services are used, then the E911 calling service will not function until power is restored. You should also be aware that after a power failure or disruption, you may need to reset or reconfigure the device prior to utilizing the service, including E911 dialing.
Internet Disruption
If your internet connection or broadband service is lost, suspended, terminated or disrupted, E911 calling will not function until the internet connection and/or broadband service is restored.
Account Suspension
If your account is suspended or terminated, then all E911 dialing services will not function.
Network Congestion
There may be a greater possibility of network congestion and/or reduced speed in the routing of E911 calls as compared to 911 dialing over traditional public telephone networks.
WAIVER
You hereby agree to release, indemnify, defend, and hold us and our officers, directors, representatives, agents, and any third party service provider that furnishes VoIP-related services to you, harmless from any and all claims, damages, losses, suits or actions, fines, penalties, costs and expenses (including, but not limited to, attorneys’ fees), whether suffered, made, instituted or asserted by you or by any other party or person (collectively, “Claims”) arising from or related to the VoIP services, including but not limited to any failure or outage of the VoIP services, incorrect routing or use of, or any inability to use, E911 dialing features. The foregoing waiver and release shall not apply to Claims arising from our gross negligence, recklessness, or willful misconduct.
Acceptable Use Policy
The following policy applies to all hosted services provided to you, including but not limited to (and as applicable) hosted applications, hosted websites, hosted email services, and hosted infrastructure services (“Hosted Services”).
Cloud Matrix IT does not routinely monitor the activity of hosted accounts except to measure service utilization and/or service uptime, security-related purposes and billing-related purposes, and as necessary for us to provide or facilitate our managed services to you; however, we reserve the right to monitor Hosted Services at any time to ensure your compliance with the terms of this Acceptable Use Policy (this “AUP”) and our master services agreement, and to help monitor and ensure the safety, integrity, reliability, or security of the Hosted Services.
Similarly, we do not exercise editorial control over the content of any information or data created on or accessible over or through the Hosted Services. Instead, we prefer to advise our customers of inappropriate behavior and any necessary corrective action. If, however, Hosted Services are used in violation of this AUP, then we reserve the right to suspend your access to part or all of the Hosted Services without prior notice.
Violations of this AUP: The following constitute violations of this AUP:
• Harmful or illegal uses: Use of a Hosted Service for illegal purposes or in support of illegal activities, to cause harm to minors or attempt to contact minors for illicit purposes, to transmit any material that threatens or encourages bodily harm or destruction of property or to transmit any material that harasses another is prohibited.
• Fraudulent activity: Use of a Hosted Service to conduct any fraudulent activity or to engage in any unfair or deceptive practices, including but not limited to fraudulent offers to sell or buy products, items, or services, or to advance any type of financial scam such as “pyramid schemes,” “Ponzi schemes,” and “chain letters” is prohibited.
• Forgery or impersonation: Adding, removing, or modifying identifying network header information to deceive or mislead is prohibited. Attempting to impersonate any person by using forged headers or other identifying information is prohibited. The use of anonymous remailers or nicknames does not constitute impersonation.
• SPAM: Cloud Matrix IT has a zero tolerance policy for the sending of unsolicited commercial email (“SPAM”). Use of a Hosted Service to transmit any unsolicited commercial or unsolicited bulk e-mail is prohibited. You are not permitted to host, or permit the hosting of, sites or information that is advertised by SPAM from other networks. To prevent unnecessary blacklisting due to SPAM, we reserve the right to drop the section of IP space identified by SPAM or denial-of-service complaints if it is clear that the offending activity is causing harm to parties on the Internet, if open relays are on the hosted network, or if denial of service attacks are originated from the hosted network.
• Internet Relay Chat (IRC). The use of IRC on a hosted server is prohibited.
• Open or “anonymous” proxy: Use of open or anonymous proxy servers is prohibited.
• Crypto mining. Using any portion of the Hosted Services for mining cryptocurrency or using any bandwidth or processing power made available by or through a Hosted Services for mining cryptocurrency, is prohibited.
• Hosting spammers: The hosting of websites or services using a hosted server that supports spammers, or which causes (or is likely to cause) our IP space or any IP space allocated to us or our customers to be listed in any of the various SPAM databases, is prohibited. Customers violating this policy will have their server immediately removed from our network and the server will not be reconnected until such time that the customer agrees to remove all traces of the offending material immediately upon reconnection and agree to allow Cloud Matrix IT to access the server to confirm that all material has been completely removed. Any subscriber guilty of a second violation may be immediately and permanently removed from the hosted network for cause and without prior notice.
• Email/message forging: Forging any email message header, in part or whole, is prohibited.
• Unauthorized access: Use of the Hosted Services to access, or to attempt to access, the accounts of others or to penetrate, or attempt to penetrate, Cloud Matrix IT’s security measures or the security measures of another entity's network or electronic communications system, whether or not the intrusion results in the corruption or loss of data, is prohibited. This includes but is not limited to accessing data not intended for you, logging into or making use of a server or account you are not expressly authorized to access, or probing the security of other networks, as well as the use or distribution of tools designed for compromising security such as password guessing programs, cracking tools, or network probing tools.
• IP infringement: Use of a Hosted Service to transmit any materials that infringe any copyright, trademark, patent, trade secret or other proprietary rights of any third party, is prohibited.
• Collection of personal data: Use of a Hosted Service to collect, or attempt to collect, personal information about third parties without their knowledge or consent is prohibited.
• Network disruptions and sundry activity. Use of the Hosted Services for any activity which affects the ability of other people or systems to use the Hosted Services or the internet is prohibited. This includes “denial of service” (DOS) attacks against another network host or individual, “flooding” of networks, deliberate attempts to overload a service, and attempts to “crash” a host.
• Distribution of malware: Intentional distribution of software or code that attempts to and/or causes damage, harassment, or annoyance to persons, data, and/or computer systems is prohibited.
• Excessive use or abuse of shared resources: The Hosted Services depend on shared resources. Excessive use or abuse of these shared network resources by one customer may have a negative impact on all other customers. Misuse of network resources in a manner which impairs network performance is prohibited. You are prohibited from excessive consumption of resources, including CPU time, memory, and session time. You may not use resource-intensive programs which negatively impact other customers or the performances of our systems or networks.
• Allowing the misuse of your account: You are responsible for any misuse of your account, even if the inappropriate activity was committed by an employee or independent contractor. You shall not permit your hosted network, through action or inaction, to be configured in such a way that gives a third party the capability to use your hosted network in an illegal or inappropriate manner. You must take adequate security measures to prevent or minimize unauthorized use of your account. It is your responsibility to keep your account credentials secure.
To maintain the security and integrity of the hosted environment, we reserve the right, but not the obligation, to filter content, Cloud Matrix IT requests, or website access for any web requests made from within the hosted environment.
Revisions to this AUP: We reserve the right to revise or modify this AUP at any time. Changes to this AUP shall not be grounds for early contract termination or non-payment.
